Enterprise software is stuck in the past, and 2026 won't wait. Your legacy web applications, which once powered business operations, now create bottlenecks, security risks, and frustrated teams trying to compete in a cloud-first world.
This guide is for IT leaders, CTOs, and decision-makers who need to transform outdated systems without breaking the bank or disrupting daily operations.
We'll walk you through the step-by-step modernization process that turns legacy applications into cloud-native powerhouses, explore critical success factors that separate failed projects from breakthrough transformations, and reveal the technology stack choices that position your organization for sustainable growth in 2026 and beyond.
The companies making this transition now are pulling ahead. The ones waiting are falling behind.
Legacy to Cloud-Native Modernization for Enterprise Web Apps
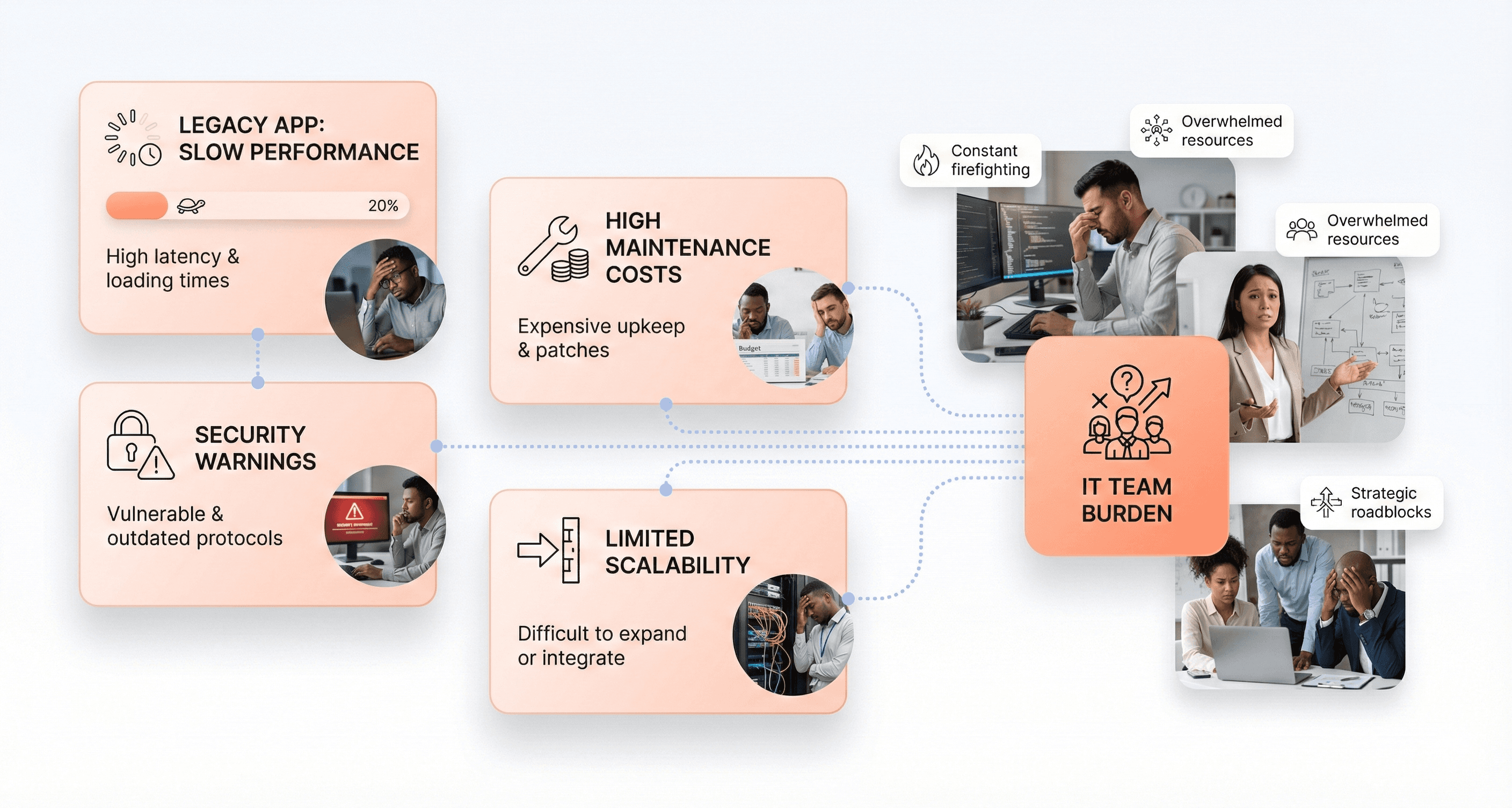
Defining Legacy Applications and Their Limitations
Legacy applications refer to systems that have been in use for an extended period and exhibit several critical characteristics that distinguish them from modern solutions. These applications typically rely on outdated technology, having been built using older development tools, programming languages, and system architectures that are no longer aligned with current industry standards and best practices.
The most significant limitations of legacy systems manifest in multiple operational areas. Performance inefficiencies are common, with these systems often suffering from slow response times that directly impact productivity and user satisfaction. Security vulnerabilities present another critical concern, as outdated security measures and lack of regular updates make these applications more susceptible to cybersecurity threats and compliance violations.
From a financial perspective, legacy applications burden organizations with escalating maintenance costs over time. The need for ongoing support, specialized expertise, and hardware maintenance creates mounting operational expenses. Additionally, these systems demonstrate limited scalability, making it challenging and expensive to accommodate growing business demands or user loads.
Perhaps most critically, legacy applications exhibit poor adaptability to changing business requirements. This inflexibility stems from tightly coupled architectures, poorly documented code, and knowledge silos that develop when original developers leave organizations. The resulting technical debt makes it extremely difficult for new team members to understand, modify, or extend these systems effectively.
Key Components of the Modernization Process
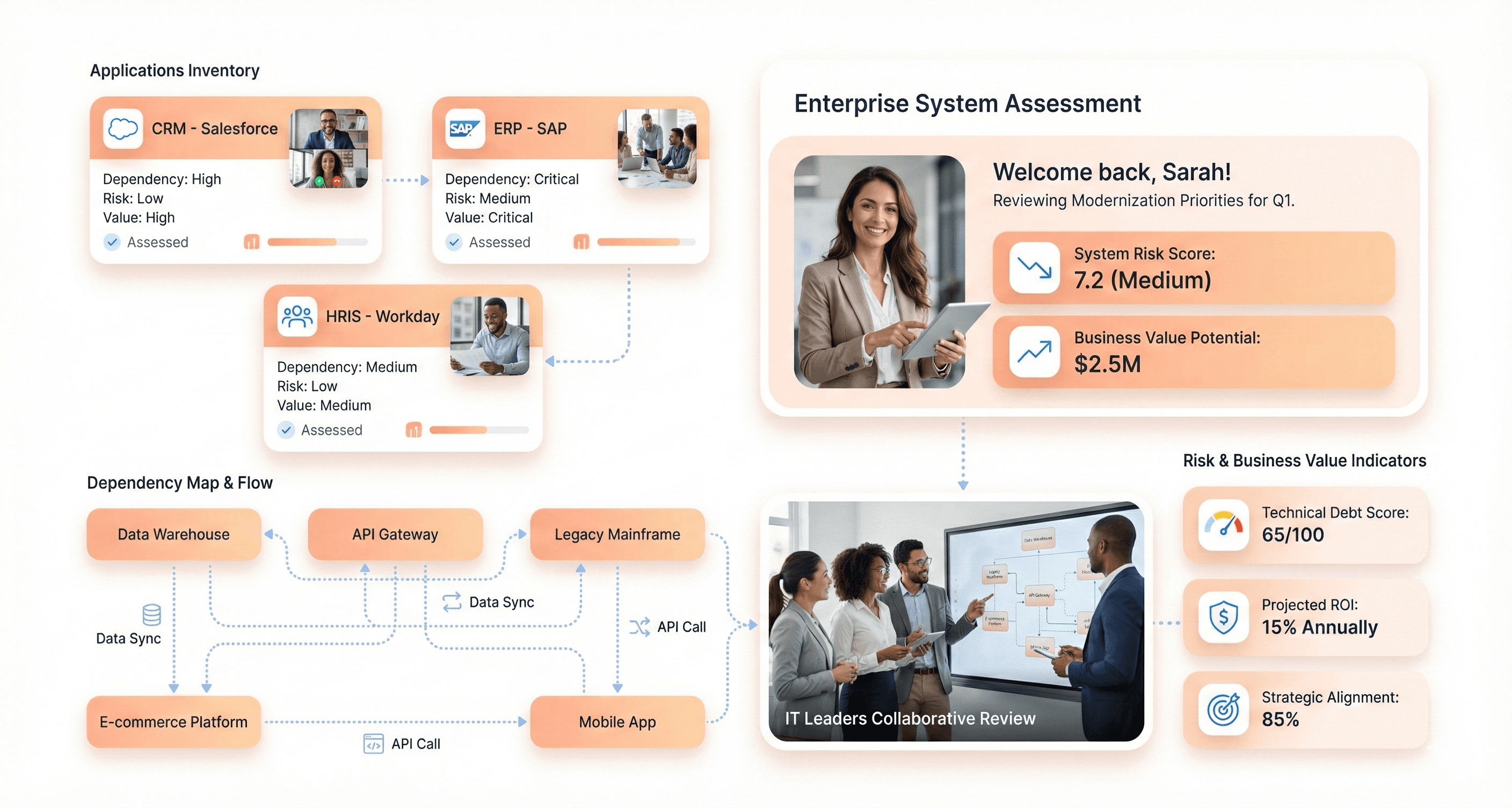
The modernization process begins with a comprehensive assessment phase that serves as the foundation for all subsequent efforts. This assessment involves taking a detailed inventory of existing applications and systems, evaluating their current state, identifying strengths and weaknesses, and pinpointing specific areas requiring improvement. Organizations must plot applications against axes of modernization difficulty and potential business value to prioritize their efforts effectively.
A critical component of successful modernization involves addressing technical debt early in the process. Technical debt represents the consequences of choosing quick solutions over comprehensive approaches, resulting in compromised code quality and architectural shortcuts. To address this systematically, organizations must prioritize debt reduction through code restructuring and refactoring while transitioning toward cloud-native systems that enhance scalability and cost-effectiveness.
The modernization process also requires establishing architectural observability to understand existing system dependencies and behaviors. This involves dependency discovery through both static code analysis and runtime analysis to reveal how systems actually behave in production. Organizations need to identify dead code, understand traffic patterns, map external dependencies, and assess potential failure modes.
Risk-based prioritization forms another essential component, where organizations plot system components against business criticality and technical risk. Components scoring high in both areas typically require encapsulation strategies rather than complete rewrites, as the risk of introducing new problems often outweighs the benefits of starting fresh.
Strategic Approaches for Different System Types
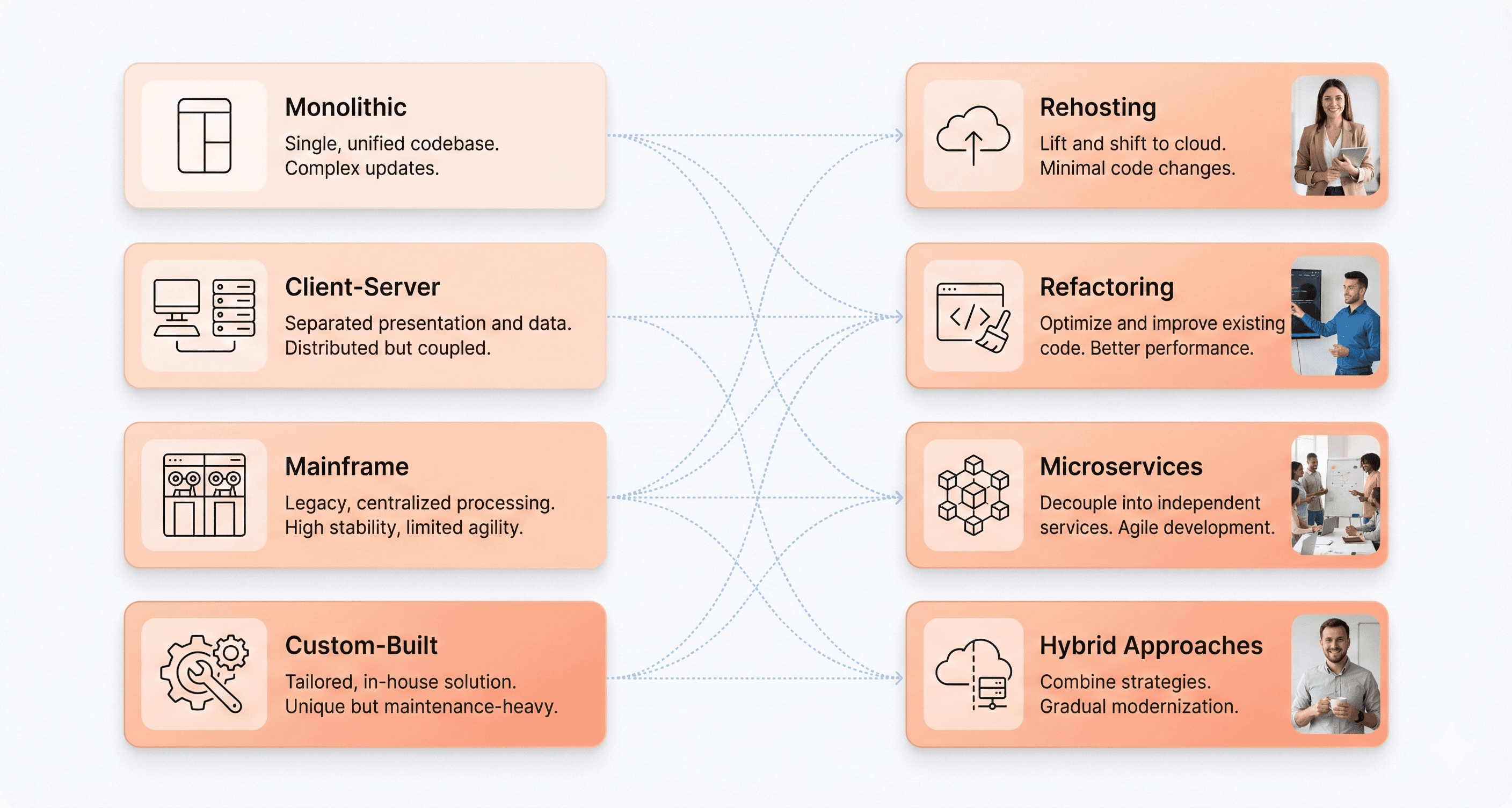
Different types of legacy systems require tailored modernization approaches based on their unique characteristics and architectural patterns. Understanding these distinctions is crucial for selecting appropriate strategies and tools.
Mainframe systems, commonly found in financial institutions and government agencies, handle high-volume processing demands and typically require strategies like rehosting or refactoring. These approaches allow organizations to leverage modern infrastructure while preserving critical functionalities that have been refined over decades of operation.
Client-server applications distribute processing between client devices and servers, making them candidates for migration to web-based or cloud-native architectures. This transformation improves accessibility and scalability while maintaining familiar operational patterns for end users.
Monolithic applications present unique challenges due to their tightly coupled architecture. Modernization often involves decomposing these systems into smaller, independent modules through microservices architecture or modular monoliths. Success requires careful analysis of business process boundaries and domain identification to ensure proper separation of concerns.
Custom-built applications demand specialized approaches due to their bespoke nature and unique business requirements. Teams may need to rearchitect specific components or implement hybrid strategies that combine multiple modernization techniques.
The selection of appropriate modernization strategies depends on several factors, including system age and complexity, organizational budget and timeline constraints, risk tolerance levels, and desired transformation outcomes. Organizations often adopt hybrid approaches, combining different strategies such as encapsulating some components while rehosting others and refactoring critical modules. This flexibility allows for phased implementations that minimize disruption while maximizing business value throughout the transformation journey.
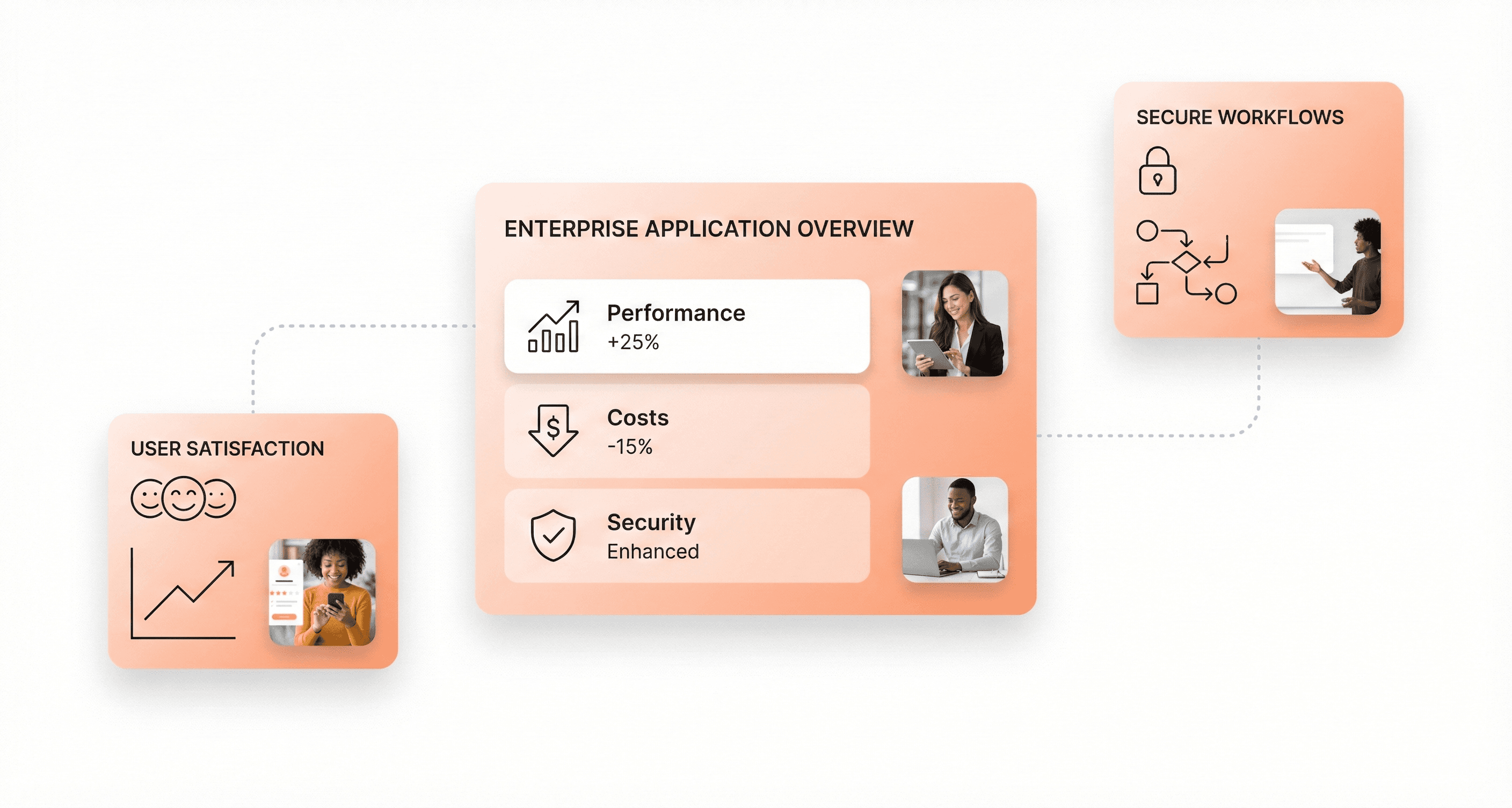
Business Benefits of Modernizing Enterprise Web Applications
Enhanced Performance and Scalability Capabilities
Modernizing enterprise web applications significantly boosts the speed and efficiency of business processes. By updating legacy systems, organizations can streamline operations, allowing for quicker responses to market changes and fostering a culture of innovation. Modernized applications leverage cloud-native architectures and containerization technologies like Docker and Kubernetes, enabling consistent environments across development, testing, and production while offering enhanced scalability, portability, and efficient resource utilization.
The performance improvements are tangible - modernized systems can reduce product development cycles, enabling enterprises to bring new offerings to market more rapidly. Cloud platforms such as AWS, Azure, and Google Cloud provide the scalability and flexibility necessary to respond more rapidly to business needs, supporting modern architectures like microservices and serverless computing.
Reduced Maintenance Costs and Technical Debt
One of the most tangible benefits of enterprise web application modernization is the significant reduction in operational costs. Organizations achieve substantial cost savings by optimizing resource use and automating routine tasks. Modernized systems require considerably less maintenance and demonstrate greater resilience, leading to lower ongoing maintenance costs, fewer system disruptions, and further cost reductions over time.
The elimination of technical debt becomes particularly valuable as legacy systems often consume substantial developer time on maintenance and bug fixing compared to feature development. By modernizing applications, enterprises can redirect their development resources toward innovation and new feature creation rather than constantly addressing legacy system issues and inefficiencies.
Improved Security and Compliance Standards
As regulatory requirements become increasingly complex, maintaining compliance presents significant challenges for large organizations. Modernized enterprise web applications incorporate automated compliance checks and streamlined reporting features, helping ensure adherence to regulations while reducing the administrative burden on compliance teams.
These enhanced security frameworks allow enterprises to stay ahead of regulatory changes with minimal disruption to business operations. Modern applications are designed with security-first principles, incorporating contemporary threat protection mechanisms and compliance frameworks that legacy systems simply cannot support effectively.
Better User Experience and Customer Satisfaction
Modernized applications dramatically enhance the customer experience by offering more user-friendly interfaces and improved functionality, along with the capability to quickly address any usability issues. This comprehensive improvement in user experience not only increases customer satisfaction but also helps retain customers in today's competitive market environment.
A compelling example demonstrates this impact: a global financial institution that modernized its core banking system achieved a 15% to 20% increase in customer satisfaction. This illustrates the tangible benefits that modernization delivers, driving both operational efficiency and enhanced customer engagement. Enterprises that prioritize modernization in customer-facing applications consistently see higher engagement rates and improved customer loyalty, directly translating into better business performance.
Enhanced Integration with Modern Technologies
Modernized web applications provide advanced data processing and analytics capabilities, enabling enterprises to derive real-time insights and make more informed strategic decisions. This enhanced data visibility supports superior strategic planning and operational efficiency, allowing businesses to identify trends, optimize processes, and predict customer needs with remarkable accuracy.
The integration of AI and machine learning tools into modernized enterprise applications enhances decision-making capabilities and automates complex business processes. AI-driven features, including predictive analytics and intelligent automation, add significant operational value, allowing enterprises to optimize their operations and deliver increasingly personalized customer experiences. Additionally, the convergence with Internet of Things (IoT) devices offers new avenues for enhancing operations, though it requires careful management of data stream complexity and security across connected devices.
Step-by-Step Legacy Modernization Process
Comprehensive Current System Assessment
Previously, I've established the importance of legacy modernization, and now we turn to the critical first step: conducting a thorough assessment of your current systems. This foundational phase determines the success of your entire modernization journey.
Legacy systems often exhibit telltale warning signs that indicate the need for modernization. Your technology stack may be running unsupported versions or outdated programming languages, leading to increased costs and security risks. System performance typically suffers from slow response times and frequent crashes, directly reducing productivity across your organization. Additionally, limited API support and manual workflows create operational inefficiencies that compound over time.
Technology Stack Evaluation
Warning Signs: Unsupported versions, outdated languages
Impact: Increased costs, security risks
System Performance Analysis
Warning Signs: Slow response times, frequent crashes
Impact: Reduced productivity
Integration Capabilities Review
Warning Signs: Limited API support, manual workflows
Impact: Operational inefficiency
Security Features Audit
Warning Signs: Outdated protocols, known vulnerabilities
Impact: Compliance challenges
Using evaluation tools like Gartner's IT assessment framework provides measurable benchmarks to gauge system performance and readiness for modernization. These tools help create a clear roadmap for improvement by monitoring key metrics, including system uptime and downtime, performance efficiency and resource utilization, maintenance expenses, and user satisfaction scores.
Business Goals and Technical Requirements Analysis
With this comprehensive assessment in mind, next, we'll examine how technical evaluations must align with your business priorities to ensure modernization efforts deliver real value. Legacy systems often struggle with downtime, security gaps, and integration hurdles that directly impact business objectives.
The alignment between technical considerations and business focus creates a strategic framework for modernization:
Business Priority | Technical Consideration | Modernization Focus |
|---|---|---|
Market Agility | Flexibility | Transition to microservices |
Cost Optimization | Operational efficiency | Move to cloud solutions |
Customer Experience | Improved performance | Enhance UI/UX design |
Innovation Capacity | Seamless integration | Adopt API-first architecture |
As IBM notes, "Modernization is not necessarily about replacing these applications entirely, but rather about revitalizing them to meet contemporary needs and standards." This philosophy emphasizes the importance of understanding both current system limitations and future business requirements before selecting an appropriate modernization strategy.
Strategic Modernization Approach Selection
Now that we have covered system assessment and business alignment, the next crucial step involves selecting the most appropriate modernization strategy. This decision can determine whether your transition is smooth or fraught with challenges.
Here's a comprehensive breakdown of common modernization strategies and their characteristics:
Strategy | Characteristics | Best For | Risk Level | Resource Requirements |
|---|---|---|---|---|
Big Bang | Full system replacement | Complete system overhaul | High | High upfront investment |
Incremental | Gradual updates | Systems that can run during updates | Moderate | Costs spread over time |
Replatforming | Shift to new infrastructure | Performance-focused improvements | Moderate | Medium investment |
Refactoring | Restructuring existing code | Systems with strong core functionality | Low | Lower initial costs |
Microservices | Breaking monolithic systems | Scalability and flexibility upgrades | Moderate | Continuous investment |
Key Selection Factors:
System Criticality: For mission-critical systems, incremental updates are often safer, as they reduce operational risks and maintain stability throughout the transition process.
Resource Availability: Evaluate your team's skills and budget constraints, considering upfront costs, team capacity, training needs, and testing timelines.
Business Impact: Assess how modernization might affect operations, including potential downtime, customer experience implications, and compliance requirements.
Implementation and Development Phase
Previously, I've outlined strategy selection, and with this foundation, next, we'll explore the implementation phase. Instead of completely replacing systems, organizations should consider a phased approach to modernization that minimizes disruption while maximizing results.
Resource Organization Framework:
Technical Infrastructure
Components: Hardware, software licenses, cloud services
Considerations: Cover initial setup and ongoing operational costs
Personnel Requirements
Components: Training, hiring, consulting
Considerations: Address skill gaps and time needed for training
Implementation Tools
Components: Development tools, testing environments
Considerations: Plan for immediate and long-term needs
Contingency Planning
Components: Risk mitigation, unexpected issues
Considerations: Set aside 15-20% of the total budget for surprises
Three-Phase Implementation Structure:
Phase 1: Assessment and Design
Analyze the current architecture and design a roadmap for the updated system. Use tools for continuous code quality checks to catch potential issues early in the development cycle.
Phase 2: Development and Testing
Start implementing the modernization plan while keeping the old system functional. Modern frameworks make it easier to integrate new components with existing ones, ensuring seamless transitions.
Phase 3: Deployment and Validation
Roll out the updated components using automated CI/CD processes to monitor stability and ensure the system runs smoothly throughout the deployment process.
Testing and Quality Assurance Procedures
Now that we have covered the implementation phases, testing and quality assurance become critical for ensuring successful modernization. Modern tools make transitions smoother by employing strategic validation approaches throughout the process.
Parallel System Operations Strategy:
Running legacy and modernized systems simultaneously allows organizations to maintain operations while syncing data between old and updated systems. This approach provides a safety net during the transition period.
Gradual Component Migration:
Leverage container orchestration to update systems one piece at a time. This methodology enables:
Seamless, step-by-step updates
Ongoing validation of system performance
Minimal impact on users
Reduced risk exposure
Continuous Performance Monitoring:
Track system health and performance metrics throughout the modernization process. This continuous monitoring helps confirm successful deployments and quickly spot any issues before they impact operations.
Deployment and Continuous Monitoring
With testing procedures established, the final phase focuses on deployment strategies that minimize disruption. Phased rollouts help reduce operational disruptions while ensuring system stability and performance.
Deployment Best Practices:
Modern deployment approaches emphasize gradual rollouts using automated processes. Automated CI/CD processes monitor stability and ensure systems run smoothly during deployment. This automation reduces human error and provides consistent, repeatable deployment procedures.
Ongoing Monitoring Framework:
Continuous monitoring becomes essential post-deployment, tracking key metrics including:
System uptime and availability
Performance efficiency and response times
Resource utilization and capacity
User satisfaction and experience metrics
Validation and Optimization:
Post-deployment validation ensures that modernized systems meet performance expectations and business requirements. Regular assessments help identify optimization opportunities and ensure the infrastructure remains competitive in an ever-changing digital landscape.
The modernization process requires thoughtful planning and execution, with success depending on identifying system weaknesses, choosing the right approach, and ensuring minimal disruption during implementation. This structured methodology creates a foundation for long-term success in digital transformation initiatives.
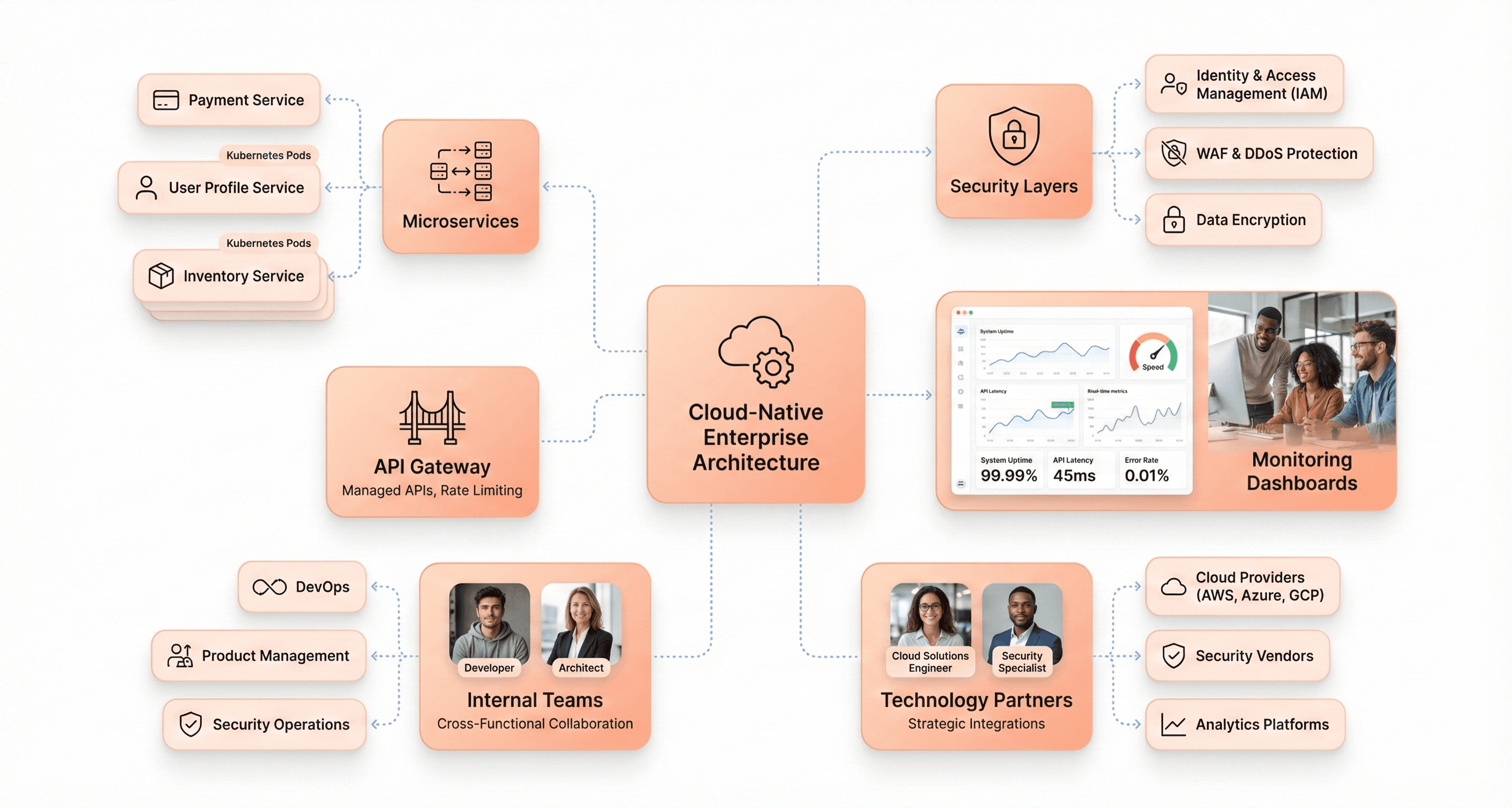
Technology Stack and Tools for Modern Web Applications
Cloud-Native Architecture and Microservices
Building modern enterprise web applications requires a fundamental shift toward cloud-native architecture patterns. The AWS Green Boost toolkit demonstrates this approach by leveraging TypeScript, AWS Cloud Development Kit (CDK), React, and Node.js to create scalable, distributed systems. Cloud-native applications are designed from the ground up to take advantage of cloud computing frameworks, utilizing services like AWS Lambda for serverless compute, Amazon Aurora PostgreSQL-Compatible Edition for managed databases, and Amazon CloudFront for global content delivery.
The architecture separates concerns through distinct layers, with AWS Lambda functions handling business logic while Amazon S3 manages static assets. This separation enables teams to develop, deploy, and scale individual components independently. The Green Boost pattern showcases how modern applications can integrate multiple AWS services seamlessly, creating a robust foundation that supports CRUD operations while maintaining high availability and performance.
Microservices architecture naturally emerges from this cloud-native approach, allowing different teams to own specific business capabilities. The reference architecture demonstrates how user requests flow through Amazon CloudFront and AWS WAF before reaching Lambda functions, which then interact with Aurora databases and other AWS services based on specific business needs.
Containerization and API-First Development
Now that we have covered the foundational architecture patterns, containerization plays a crucial role in modern application deployment strategies. While the reference implementation focuses on serverless Lambda functions, the underlying principles support containerized workloads through consistent packaging and deployment mechanisms.
The Green Boost framework emphasizes API-first development through its structured approach to building CRUD applications. The toolkit generates standardized API interfaces that enable frontend and backend teams to work independently. This approach is evident in the separation between the React-based UI components and the Node.js backend services, connected through well-defined API contracts.
The development workflow supports this API-first methodology through integrated tooling. The framework includes ESLint for static code analysis, Prettier for code formatting, and TypeScript for type safety across the entire stack. These tools ensure consistency and reliability in API development, reducing integration issues between different application layers.
Package management through pnpm and workspace configuration demonstrates modern dependency management practices. The monorepo structure allows teams to share common configurations while maintaining clear boundaries between different application components, supporting both containerized and serverless deployment patterns.
AI-Based Automation and Analytics Integration
Previously, I've established how cloud-native architecture provides the foundation for modern applications. The integration of AI-based automation and analytics becomes seamless within this framework through AWS's comprehensive service ecosystem. Amazon CloudWatch serves as the central monitoring and observability platform, collecting metrics from Lambda functions, Aurora databases, and CloudFront distributions.
The Green Boost pattern incorporates automated monitoring through the cdk-monitoring-constructs library, which creates comprehensive dashboards and alerting mechanisms. This automation extends to infrastructure management, where AWS CDK enables infrastructure-as-code practices that automatically provision and configure resources based on application requirements.
Analytics integration occurs through Amazon Simple Notification Service (SNS) for event-driven architectures and CloudWatch for real-time metrics collection. The framework automatically captures application performance data, database query metrics, and user interaction patterns. These analytics capabilities support data-driven decision making and automated scaling based on usage patterns.
Vulnerability management automation is built into the development workflow through pnpm audit commands and cdk-nag static analysis tools. These automated security checks prevent vulnerabilities from reaching production environments while maintaining development velocity.
Modern Security and Monitoring Solutions
With this foundation of automation in mind, security becomes a multi-layered concern addressed through integrated AWS services and development practices. AWS WAF provides the first line of defense, filtering malicious requests before they reach application resources. This web application firewall integrates seamlessly with CloudFront distributions, providing global protection against common attack vectors.
AWS Secrets Manager eliminates hardcoded credentials from application code, enabling secure access to database connections and API keys through programmatic retrieval. The Green Boost pattern demonstrates this through its Aurora database configuration, where connection strings and authentication credentials are stored securely and accessed only when needed.
Network security is enhanced through Systems Manager Session Manager, which provides secure shell access to EC2 bastion hosts without exposing public IP addresses. This approach demonstrates how modern security practices eliminate traditional attack vectors while maintaining operational flexibility for database administration and troubleshooting.
Monitoring solutions extend beyond basic metrics collection through comprehensive dashboard creation and alerting mechanisms. The cdk-monitoring-constructs library automatically generates CloudWatch dashboards that track key performance indicators across the entire application stack. Alert configuration enables proactive incident response, with SNS integration providing immediate notification of system anomalies or performance degradation.
The security-first approach includes static code analysis through ESLint rules and pre-commit hooks powered by Husky, ensuring that security best practices are enforced throughout the development lifecycle rather than as an afterthought during deployment.
Selecting the Right Modernization Strategy
Factors Influencing Strategy Selection
Now that we have covered the modernization process, the next critical step involves selecting the most appropriate strategy for your enterprise. Several key factors must be carefully evaluated to ensure successful legacy system transformation.
Business Requirements and Objectives form the foundation of strategy selection. Organizations must first assess what their business truly requires - whether the goal is improving performance, reducing costs, enhancing security, or adding new features. Different modernization strategies come with varying levels of complexity, cost, and risk, making it essential to align the chosen approach with specific business needs.
System Health and Current State significantly impact strategy choice. Is the legacy software functional but sluggish, or has it become a critical bottleneck? Organizations with reliable, secure, and high-performing legacy systems running on expensive, proprietary hardware may benefit more from rehosting approaches rather than complete application rewrites.
Resource Availability and Technical Expertise plays a crucial role in decision-making. Finding skilled experts familiar with older programming languages becomes increasingly difficult and expensive. Organizations must consider whether they have the internal capabilities to manage complex transformations or if they need to partner with legacy modernization services providers.
Integration Requirements determine how well legacy applications must work with modern tools and systems. Legacy systems that struggle to integrate with contemporary software create workflow bottlenecks and data silos, requiring strategies that address these connectivity challenges.
Refactoring vs Rearchitecting vs Rebuilding Decisions
Previously, we've established that modernization offers multiple pathways. Understanding when to choose refactoring, rearchitecting, or rebuilding requires careful analysis of each approach's benefits and limitations.
Refactoring focuses on restructuring and optimizing existing code without changing its external behavior. This legacy code modernization approach enhances system flexibility and allows for easier adaptation to current conditions. Refactoring works best for applications that function properly but have performance issues or maintenance difficulties. The approach enhances code quality and maintainability while aligning the codebase with current software development practices. However, refactoring can be time-consuming and costly, and may not suffice for systems with fundamental architectural issues.
Rearchitecting involves restructuring applications to embrace cloud-native architectures, microservices, or containerization. This approach becomes necessary when legacy application architecture is so outdated it cannot work with modern frameworks. Rearchitecting enhances system flexibility and scalability while facilitating integration with other systems and technologies. Companies transitioning from containers to microservices particularly benefit from this strategy. The downside includes implementation complexity and the requirement for significant changes to the existing system architecture.
Rebuilding or rewriting means developing new applications from scratch while maintaining the requirements and functionalities of legacy systems. This approach allows for creating highly efficient, state-of-the-art applications where developers can avoid past mistakes and implement best practices. However, rebuilding is time-consuming, expensive, and risky, requiring extensive testing to match previous functionalities.
Risk Assessment and Business Continuity Planning
With these strategic options in mind, risk assessment becomes paramount in modernization planning. Organizations must weigh multiple risk factors that could impact business operations during and after transformation.
Operational Impact Risks represent the most immediate concern. Modernization approaches involving modifications to legacy software or creating entirely new systems often necessitate large-scale retraining of administrators and end users. This creates significant operational challenges as employees must balance training with regular tasks, resulting in resource, productivity, and time drains that ultimately impact the bottom line.
Data Migration Risks carry inherent dangers during the transformation process. Transferring sensitive business information from legacy systems to new platforms requires careful planning and execution. Data loss, corruption, or security breaches during migration can have devastating consequences for business continuity.
Downtime and Service Interruption Risks worry business leaders significantly. Organizations fear service interruptions during transformation, particularly when dealing with mission-critical applications. The potential for system failures during migration can disrupt customer service, halt business processes, and damage reputation.
Technical Implementation Risks vary by chosen strategy. While rearchitecting, recreating, or purchasing new applications might seem appealing due to added features, these strategies are time-consuming, costly, and carry high risk levels. The complexity of implementing new architectures or technologies can lead to project delays, budget overruns, and functionality gaps.
Skill Gap Risks create additional challenges. Finding experts who understand both legacy and modern technologies proves increasingly difficult. This skills shortage can lead to implementation delays, increased costs, and potential quality issues if organizations cannot secure appropriate expertise.
Budget and Timeline Considerations
Now that we have covered risk factors, budget and timeline considerations become critical determinants in strategy selection. Different modernization approaches require varying financial investments and time commitments.
Cost Variations by Strategy differ significantly across approaches. Rehosting or "Lift and Shift" emerges as the most cost-effective and quick legacy modernization approach, minimizing code modifications and reducing project complexity. This strategy ensures faster implementation with less risk compared to other options. Refactoring approaches require moderate investment but can be time-consuming and costly depending on code complexity. Rebuilding represents the most expensive option, demanding significant time and financial resources for development, testing, and deployment.
Timeline Implications vary dramatically between strategies. Lift and Shift approaches offer the fastest path to modernization without requiring deep technical expertise. Organizations can complete migrations quickly while maintaining business continuity. Refactoring projects typically require longer timelines due to the detailed code analysis and restructuring involved. Rebuilding projects demand the longest timelines, often requiring months or years to complete, depending on application complexity.
Resource Allocation Requirements must align with organizational capabilities. Some modernization strategies require dedicated development teams, specialized expertise, and extended project management resources. Organizations must evaluate whether they have sufficient internal resources or need to engage external legacy modernization services providers.
Return on Investment Considerations help justify modernization investments. While comprehensive strategies like rebuilding require higher upfront costs, they may deliver greater long-term benefits through improved performance, reduced maintenance costs, and enhanced scalability. Simpler approaches like rehosting provide quicker ROI through immediate infrastructure cost reductions and improved system reliability.
Budget Risk Mitigation requires careful planning and contingency allocation. Without proper scoping and planning, modernization projects can exceed planned costs significantly. Organizations should allocate 10-20% contingency budgets and establish clear project scope boundaries to prevent budget overruns that threaten project success.
Partnering with Expert Modernization Services
Benefits of Working with Technology Partners
Now that we have covered the technical aspects and strategies of modernization, partnering with experienced technology consulting firms becomes crucial for successful transformation. Working with expert modernization services provides organizations with access to specialized knowledge and proven methodologies that significantly reduce project risks and accelerate time-to-value.
Technology partners bring comprehensive consulting capabilities that combine strategic thinking with hands-on implementation expertise. These partnerships enable organizations to access a complete range of services from initial assessment and strategy development through full-scale implementation and ongoing support. The collaborative approach allows internal teams to focus on core business operations while leveraging external expertise for complex technical challenges.
Expertise in Legacy Technologies and Modern Practices
Enterprise modernization consultants possess deep experience across both traditional IT ecosystems and cutting-edge modern technologies. This dual expertise is essential for successful digital transformation, as consultants must understand existing legacy systems before architecting cloud-native solutions.
Consulting teams typically include specialized roles such as Application Architects, Technical Architects, Cloud Engineers, Cloud Architects, and DevOps Engineers. Each role brings specific expertise in different aspects of modernization, from application portfolio strategy to cloud migration and automation implementation. This diverse skill set ensures comprehensive coverage of all technical domains involved in enterprise transformation.
The combination of legacy system knowledge and modern practices allows consulting partners to design optimal migration paths that preserve business continuity while enabling future innovation. Their experience with industry compliance requirements, cybersecurity vulnerabilities, and employee adoption challenges helps organizations navigate complex transformation requirements effectively.
Minimizing Operational Risks During Transition
Professional modernization services play a critical role in risk mitigation throughout the transformation process. Most organizations spend over 70% of their IT budget on maintaining existing systems, making technical debt a significant roadblock to transformation and a substantial risk during economic downturns.
Expert partners help organizations understand their current technology landscape, IT maturity levels, gaps, and potential solutions through comprehensive assessments. This thorough evaluation enables the development of strategic roadmaps that address immediate operational needs while building toward long-term modernization goals.
By leveraging proven methodologies and best practices, consulting partners minimize disruption to daily operations during the transition period. Their experience across multiple modernization projects provides valuable insights into common pitfalls and effective mitigation strategies.
Ensuring Smooth Migration and Integration
Technology modernization teams apply deep technology, data, cloud, and automation experience combined with fresh strategic thinking to ensure seamless system integration. The integration process requires careful coordination between legacy systems and modern platforms to maintain data integrity and business functionality.
Consulting partners provide end-to-end support throughout the migration process, from initial planning through final implementation and post-migration optimization. Their expertise in data integration, content management, and advanced analytics ensures that organizations can leverage their modernized systems for measurable business results.
The partnership approach enables organizations to achieve value-driven innovation while addressing ongoing operational and competitive challenges. By combining business proficiency with cutting-edge technology innovations, these collaborations help organizations implement scalable, efficient solutions that drive long-term success.
Conclusion
Legacy application modernization isn't just a technical upgrade. It's a strategic business imperative for 2026 and beyond. Organizations that embrace this transformation gain improved performance, enhanced security, reduced operational costs, and the agility to integrate modern technologies like AI and cloud services. The step-by-step approach outlined, from initial assessment through deployment and monitoring, provides a clear roadmap for organizations ready to break free from the constraints of outdated systems.
The competitive landscape of 2026 will favor businesses that can adapt quickly, scale efficiently, and deliver exceptional user experiences. By partnering with experienced modernization services and selecting the right strategy for your specific needs, you can transform legacy systems from operational burdens into strategic assets. The time to act is now, modernizing your enterprise web applications today positions your organization for sustained growth, innovation, and market leadership in an increasingly digital world.

About the author
Author Name:
Parth G
|
Founder of
Hashbyt
I’m the founder of Hashbyt, an AI-first frontend and UI/UX SaaS partner helping 200+ SaaS companies scale faster through intelligent, growth-driven design. My work focuses on building modern frontend systems, design frameworks, and product modernization strategies that boost revenue, improve user adoption, and help SaaS founders turn their UI into a true growth engine.







