
Your outdated software systems are costing your business more than you think. Legacy systems drain an average of $40,000 per year in maintenance costs alone, while security vulnerabilities put you at risk for data breaches that cost $4.4 million on average.
This guide is for CTOs, IT directors, and business leaders at SaaS companies who need to modernize aging systems but aren't sure where to start. You'll discover what legacy modernization services actually include, why a frontend-first approach works best for SaaS businesses, and how to avoid common pitfalls that derail modernization projects.
We'll cover the core modernization strategies that deliver real ROI, the technology stack powering modern SaaS architecture, and a proven execution framework that keeps your business running while you transform your systems. You'll also learn how to pick the right modernization partner and overcome the biggest challenges that trip up most companies during their transformation journey.
Understanding Legacy Systems and Their Business Impact
What Are Legacy Systems and Why They Persist in Enterprise Environments
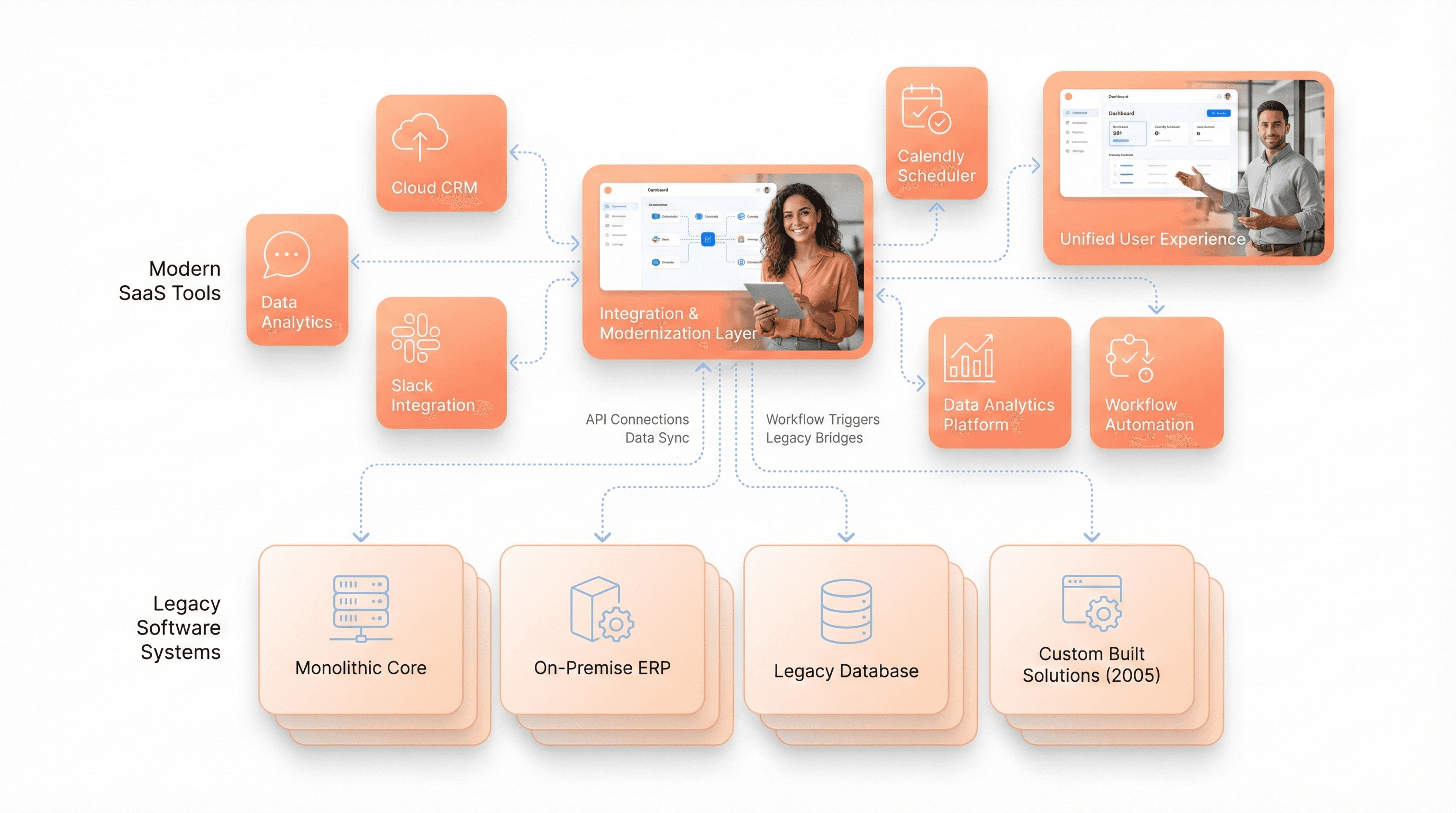
Legacy systems are outdated technology infrastructure that organizations continue to use despite newer, more advanced alternatives being available. These systems were often cutting-edge when first implemented but have become obsolete over time as technology evolved. Legacy systems encompass everything from decades-old COBOL programming languages in banking to outdated electronic health record systems in healthcare, and antiquated manufacturing software that relies heavily on spreadsheets.
The persistence of legacy systems across enterprise environments stems from several critical factors. As Nick Godfrey from Google Cloud explains, "It's actually quite hard to fully demise previous versions of technology as we adopt new versions, and so you end up with the sort of layering of various ages of all the technologies." This layering effect creates complex technology stacks where old and new systems coexist.
Organizations often struggle to replace these systems because they represent integral operational technology necessary for business continuity. Austin Allen from Airlock Digital illustrates this challenge: "The hardest way to drive the car is when you're trying to change the tire at the same time." The fear of downtime, which can cost millions of dollars per hour depending on the company, makes executives hesitant to pursue modernization initiatives.
The Government Accountability Office identified 10 critical federal IT legacy systems ranging from 8 to 51 years old, costing approximately $337 million annually to operate and maintain. Similarly, 74% of manufacturing and engineering companies continue operating with legacy systems and spreadsheets, demonstrating how widespread this challenge has become across industries.
The Hidden Costs of Maintaining Outdated Technology Infrastructure
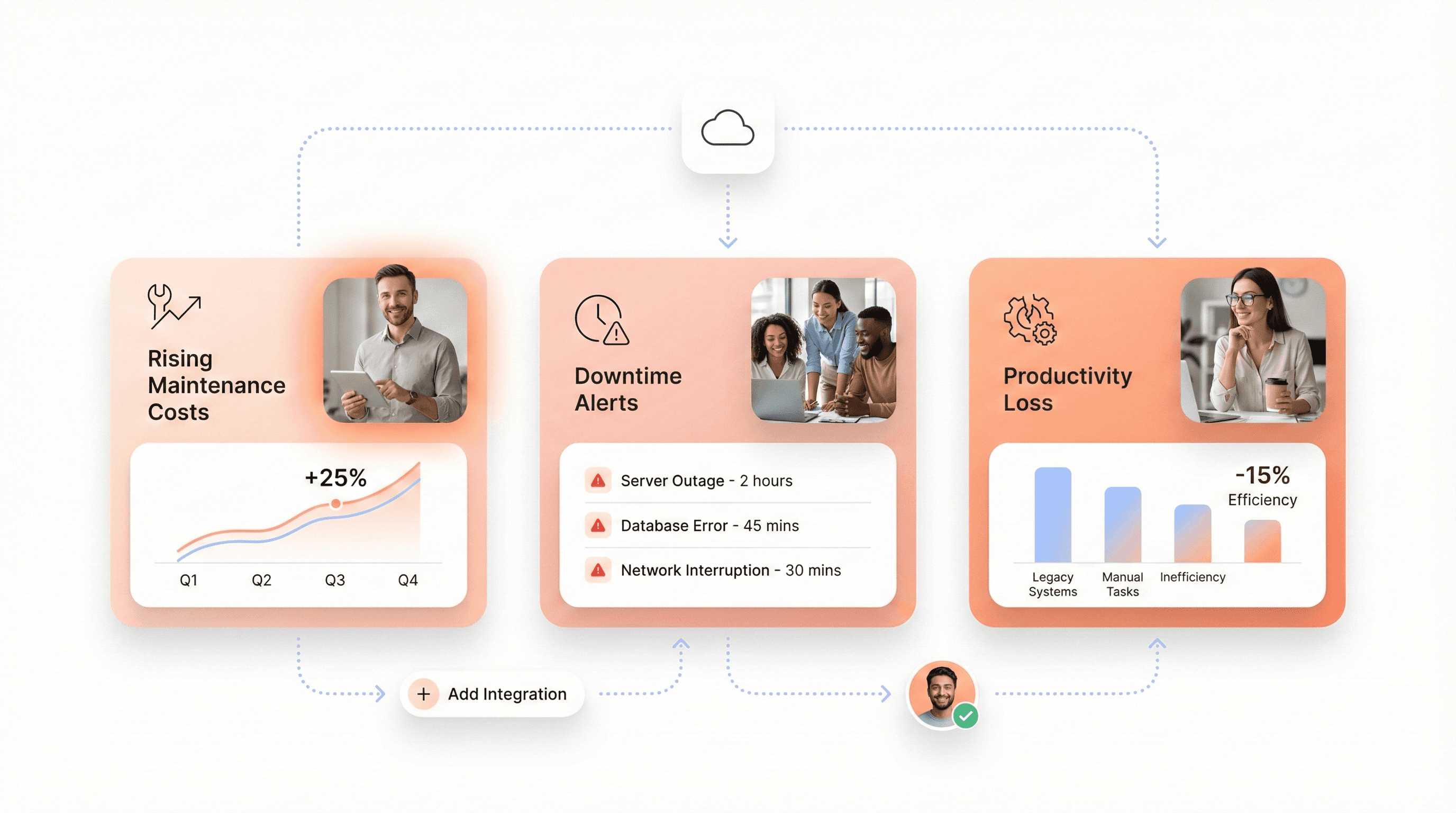
The financial burden of legacy system maintenance extends far beyond initial operational costs. Organizations spent an average of $2.7 million to overhaul legacy technology in 2023, according to SnapLogic research. However, these visible modernization costs pale in comparison to the hidden expenses of maintaining outdated infrastructure.
Legacy systems demand specialized knowledge that becomes increasingly scarce and expensive over time. Finding reliable support for decades-old technology requires hiring experts who command premium rates or maintaining internal teams with obsolete skillsets. As Godfrey points out, organizations end up requiring "a very complex skills requirement inside of your organization to be able to manage very old types of technologies through to cutting-edge technologies."
Maintenance costs escalate as legacy systems experience more frequent breakdowns and require manual workarounds for integration with modern tools. These systems often lack interoperability with newer software, forcing organizations to invest in custom bridges and middleware solutions. The inefficiency created by slow performance and clunky interfaces reduces employee productivity, while unintuitive tools lead to user frustration and decreased morale.
Unexpected downtime represents another significant hidden cost. When legacy systems fail, they can cause operational disruptions that affect customer service, revenue generation, and business reputation. The ripple effects of these disruptions often cost more than the systems themselves, as organizations scramble to implement emergency fixes while business operations suffer.
Security Vulnerabilities and Compliance Risks in Legacy Environments
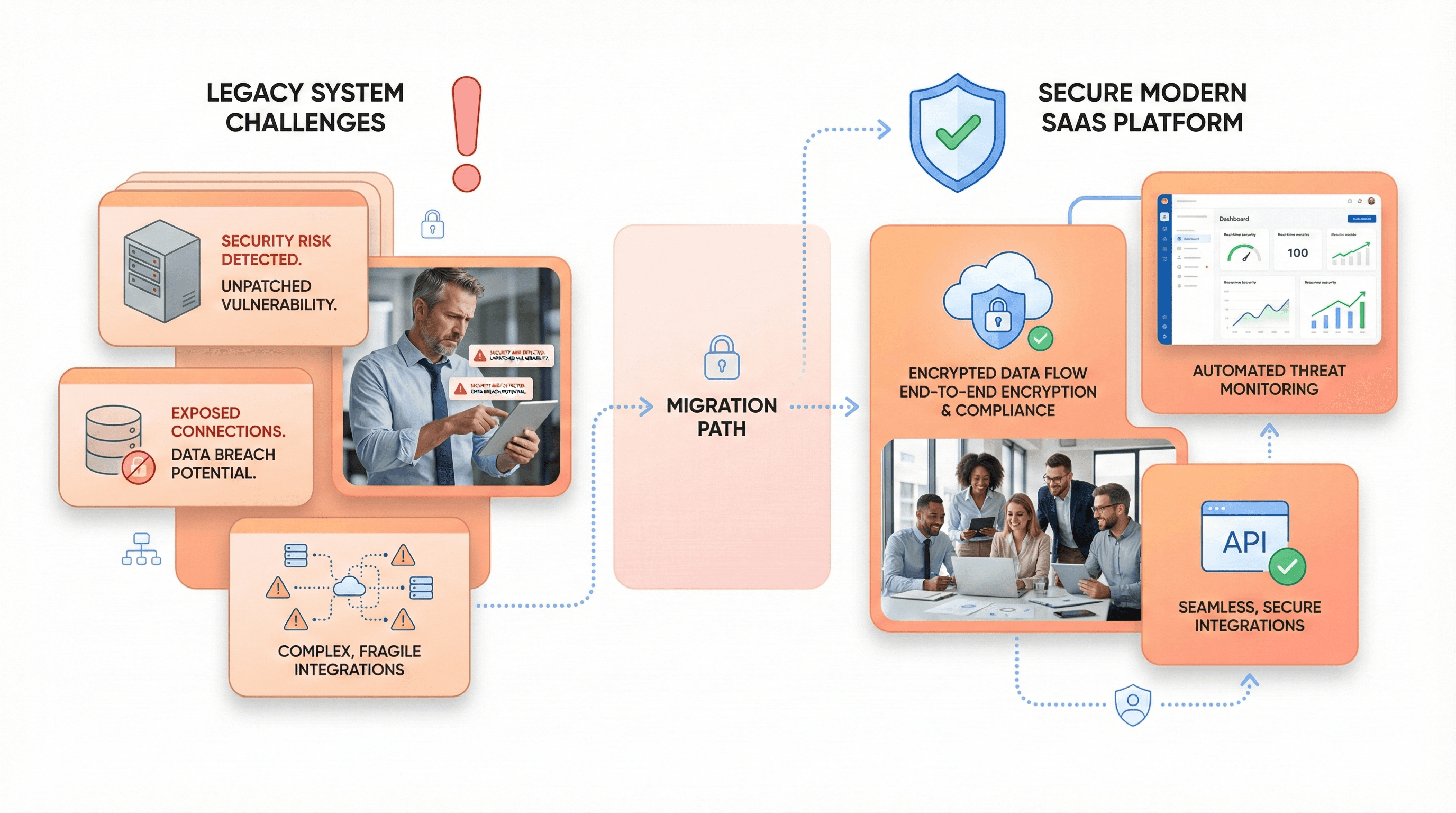
Legacy systems pose substantial security risks due to their outdated design and lack of current protection mechanisms. As Godfrey emphasizes, "This technology was designed and installed many, many years ago when the threat profile was significantly different. It is creating an ever more complex surface area." These systems lack modern security patches and protections, making them attractive targets for cybercriminals.
The average cost of a data breach reached $4.88 million in 2024 according to IBM's Cost of a Data Breach Report, making security vulnerabilities in legacy systems a critical business concern. Outdated software often cannot receive security updates, leaving organizations exposed to known vulnerabilities that malicious actors can exploit for lateral movement throughout the network.
Compliance risks compound these security challenges as industry standards evolve faster than legacy systems can adapt. Organizations relying on outdated technology struggle to meet current regulatory requirements, potentially facing fines, legal action, and reputational damage. The rigid nature of legacy systems makes implementing necessary compliance controls difficult or impossible without significant workarounds.
To mitigate these risks while legacy systems remain in place, security teams must implement compensating controls and isolate these systems from the broader network. Allen recommends that "legacy systems really should be hardened from the operating system side. You should be turning off operating system features that do not have any business purpose in your environment by default." Zero-trust access controls and continuous monitoring become essential for managing the security risks that legacy systems introduce.
Regional Drivers for Modernization Across USA, UAE, UK, and Australia
The urgency for legacy modernization varies significantly across regions, driven by different regulatory environments, competitive pressures, and digital transformation initiatives. In the United States, federal mandates and cybersecurity requirements create strong modernization drivers, particularly following high-profile government system breaches and the GAO's identification of critical legacy systems consuming hundreds of millions in annual maintenance costs.
Financial institutions across all four regions face similar pressures to modernize COBOL-based systems, but regulatory timelines and compliance requirements differ. The UAE's Vision 2071 and digital government initiatives create unique modernization pressures as organizations align with national digital transformation goals. Similarly, the UK's post-Brexit regulatory environment and focus on financial technology innovation drive banking and fintech companies toward legacy modernization services.
Australia's focus on data sovereignty and cybersecurity, particularly in government and critical infrastructure sectors, creates specific modernization requirements that differ from other regions. Healthcare systems across all four regions share common challenges with outdated electronic health record systems, but privacy regulations like GDPR in the UK create additional compliance pressures for modernization.
Manufacturing companies in these regions face varying competitive pressures based on local market conditions and supply chain requirements. The 74% of manufacturing companies still relying on legacy systems must balance modernization costs against competitive pressures that differ significantly between mature markets like the USA and UK versus rapidly developing regions like the UAE.
Defining Legacy Modernization and Its Strategic Value
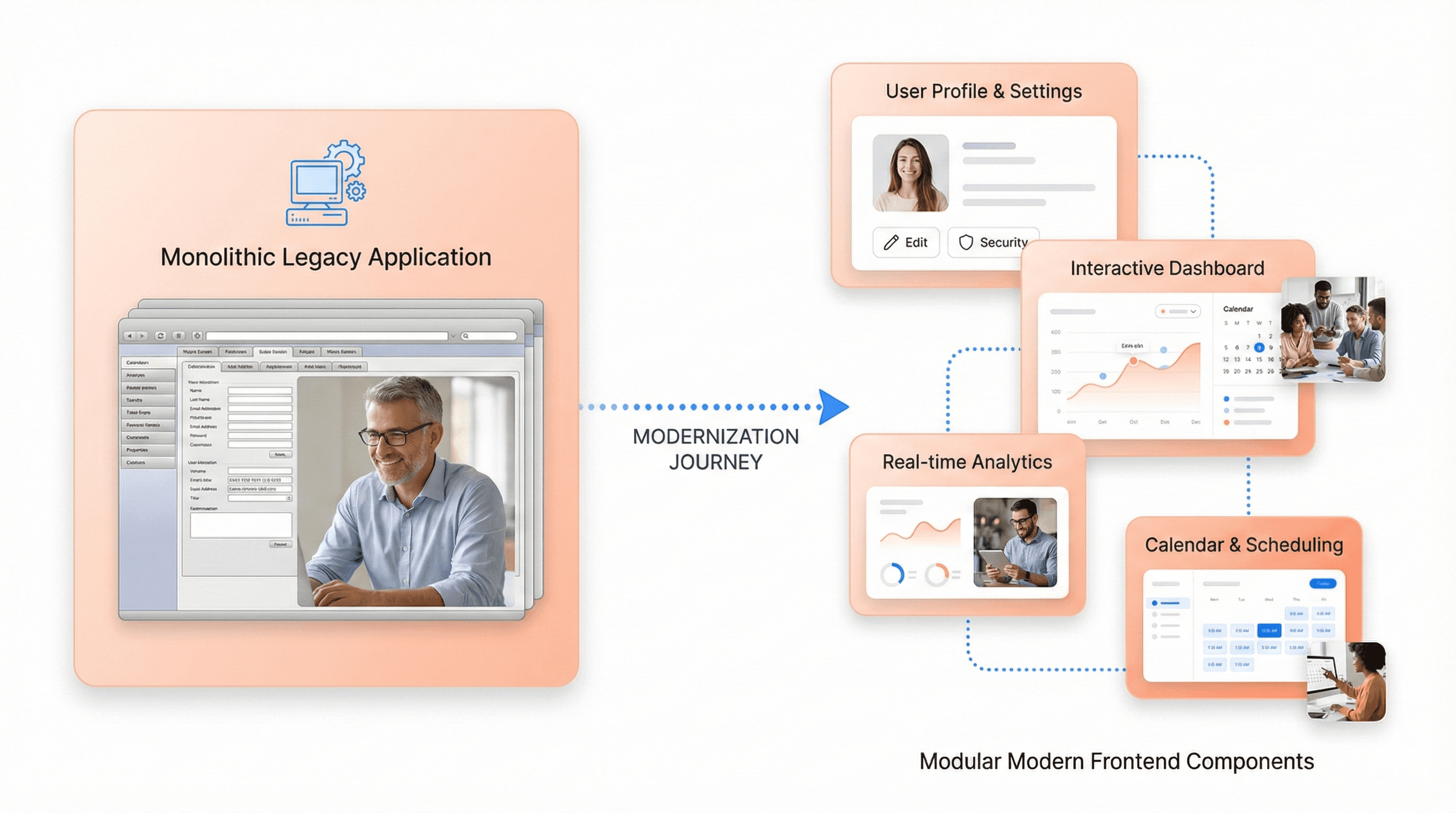
Core Components of Legacy Modernization vs Digital Transformation
Legacy modernization is the specific process of upgrading or transforming outdated, often monolithic and inefficient legacy systems into more contemporary, efficient and adaptable solutions. While digital transformation represents a broader initiative using digital technologies to create new business processes and customer experiences, legacy modernization services focus specifically on revitalizing existing applications to meet contemporary needs and standards.
The core distinction lies in scope and approach. Digital transformation encompasses the integration of digital technologies and customer-centric approaches across entire organizations, while legacy modernization targets specific applications that exhibit outdated technology, inefficient performance, and security vulnerabilities. Modern legacy modernization strategies involve developing solid application modernization approaches that guide organizations through adopting microservices, encapsulating legacy software, and introducing modernization solutions.
Business Benefits: Cost Reduction, Performance, and Innovation
Legacy modernization services deliver substantial business value through multiple performance and cost optimization channels. Organizations experience improved performance and operational efficiency, resulting in quicker response times and enhanced user experience. The modernization process significantly reduces maintenance costs while optimizing hosting capabilities and better leveraging global workforce resources, leading to substantial long-term cost savings.
Performance improvements manifest through the transition from monolithic applications to microservices architecture, where large applications are broken down into smaller, more manageable components. This approach enhances maintainability and enables better resource allocation. Additionally, modernized systems demonstrate superior scalability capabilities, addressing the limitations of legacy applications that struggle to accommodate growing business demands.
Cost efficiency emerges from eliminating the high maintenance expenses associated with outdated technology and the constant support requirements of legacy systems. Organizations also benefit from reduced technical debt - the accumulated consequences of choosing quick solutions over comprehensive approaches that typically plague legacy systems.
Enhanced Security and Compliance Through Modern Architecture
Modern architecture fundamentally transforms security posture by addressing the inherent vulnerabilities present in legacy systems. Legacy applications typically suffer from outdated security measures and lack of regular updates, making them more susceptible to cybersecurity threats. Legacy modernization services integrate security measures from the beginning of the transformation process, making security a core component of the application's architecture and design.
Modernization provides opportunities to implement comprehensive security risk assessments that identify potential threats and establish clearly defined security requirements covering data protection, access controls, encryption, and regulatory compliance. The process ensures that modernized systems comply with relevant regulations while establishing regular processes to maintain ongoing compliance standards.
Enhanced security measures include the development of application programming interfaces (APIs) that enable secure connections between modernized systems and existing applications. These APIs are crucial for enabling safe integration and interaction of various software systems, services, and platforms within the broader organizational ecosystem.
Improved Customer Experience and Competitive Advantage
Legacy modernization services directly impact customer satisfaction through comprehensive user interface and user experience improvements. Modernization efforts often involve revamping the entire user interface, contributing to increased customer and employee satisfaction through more intuitive and responsive interactions.
The competitive advantage emerges from the ability to adapt quickly to changing business requirements. Legacy applications typically demonstrate poor adaptability, making them ill-suited for modern, dynamic organizations. Modernized systems enable organizations to remain competitive in today's fast-paced business environment by providing the flexibility needed to respond to market changes and customer demands.
Future-proofing capabilities represent another significant competitive advantage. Modernized applications can incorporate advanced technologies like automation, artificial intelligence, and cloud computing solutions. This technological integration delivers enhanced features and capabilities while ensuring that organizations can leverage emerging technologies as they become available, maintaining their competitive edge in rapidly evolving markets.
Strategic Modernization Approaches and Methodologies
The Seven R's Framework for Legacy Transformation
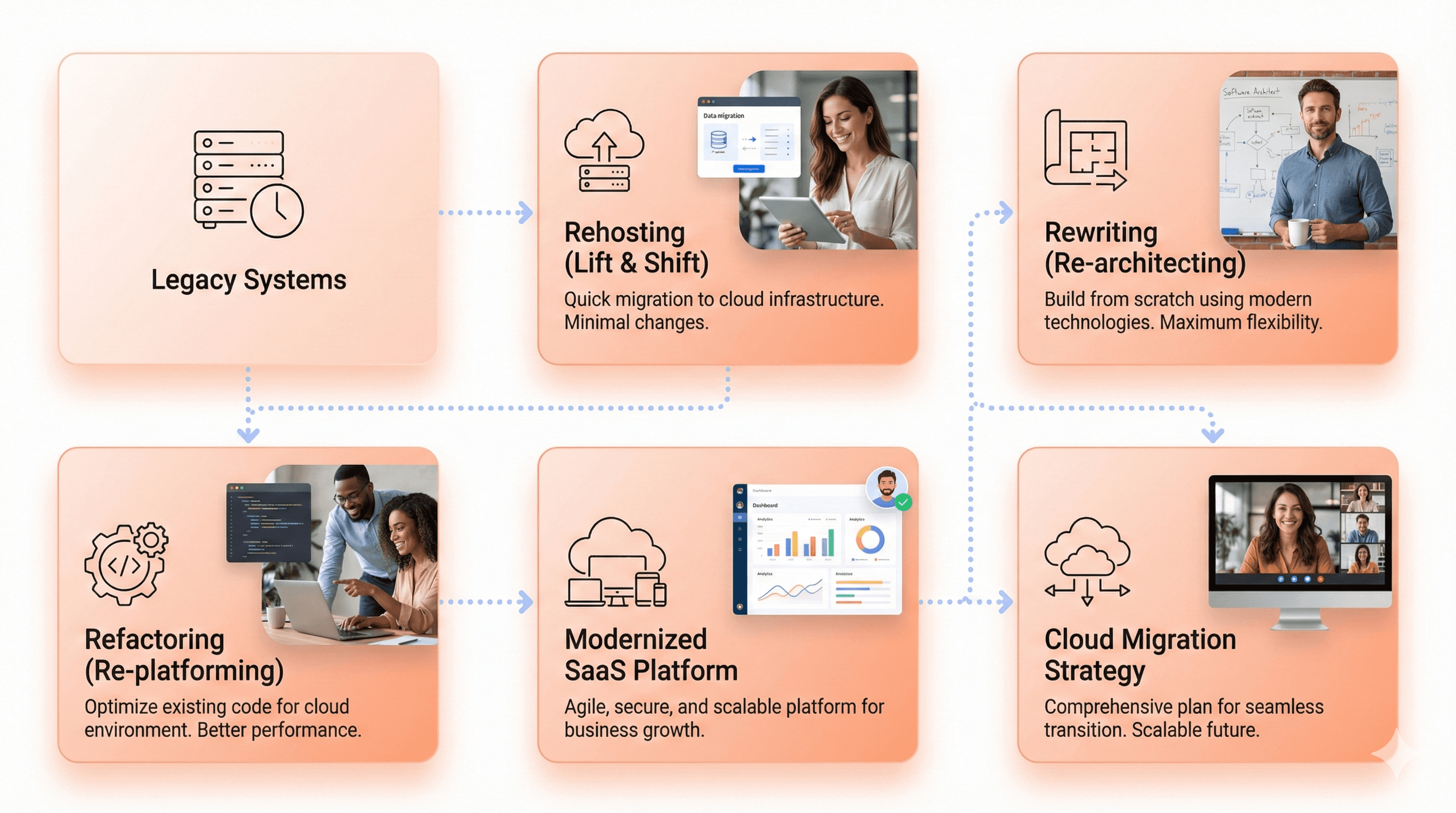
The Seven R's framework provides a comprehensive methodology for approaching legacy modernization services. This strategic framework encompasses Rehosting (lift and shift), Refactoring (re-architecting), Rewriting (rebuilding from scratch), Encapsulation, API modernization, Cloud Migration, Service-Oriented Architecture (SOA), and Replacing with new applications.
Each approach within this framework serves distinct business scenarios and technical requirements. Rehosting offers the fastest path to modernization by moving applications to new infrastructure without code changes, making it ideal for organizations prioritizing speed and minimal risk. Refactoring enhances code quality and maintainability while aligning with current development practices, though it requires more time and investment.
Rewriting provides the opportunity to leverage modern frameworks and eliminate legacy constraints entirely, but comes with higher costs and risks. Encapsulation preserves core system components while creating new interfaces through APIs, allowing gradual modernization. API modernization enables integration with modern systems without extensive code changes, while Cloud Migration enhances scalability and reduces infrastructure costs.
Lift and Shift vs Full Overhaul: Choosing the Right Strategy
The choice between lift and shift and full overhaul represents one of the most critical decisions in legacy modernization services. Lift and shift (rehosting) involves redeploying application components to different infrastructure without altering code or features, offering a cost-effective and quick modernization approach that minimizes complexity and ensures optimal business continuity.
This strategy proves particularly valuable when legacy systems are reliable and high-performing but run on expensive, proprietary hardware platforms. Organizations can maintain existing functionality while moving to modern infrastructure, with end users remaining unaware of the underlying platform changes.
Full overhaul strategies, including rewriting or replacing entire systems, provide opportunities to leverage cutting-edge technologies and eliminate architectural debt. However, these approaches are time-consuming, expensive, and carry significant risks. They often require extensive retraining of administrators and end users, creating operational challenges that can drain resources and impact productivity.
The decision matrix should consider factors including time constraints, budget limitations, risk tolerance, and the current state of legacy infrastructure. Organizations seeking rapid modernization with minimal disruption typically benefit from lift and shift approaches, while those requiring fundamental architectural changes may justify full overhaul investments.
Infrastructure Modernization vs Application Modernization Considerations
Infrastructure modernization and application modernization represent two distinct yet interconnected approaches within legacy modernization services. Infrastructure modernization focuses on updating the underlying hardware, platforms, and hosting environments while preserving existing applications and their core functionalities.
This approach addresses scenarios where legacy systems run on outdated hardware that vendors no longer support, making maintenance difficult and costly. By modernizing infrastructure first, organizations can improve system performance, enhance security, and reduce operational costs without disrupting established business processes.
Application modernization involves updating the software itself through refactoring, rewriting, or replacing applications entirely. This strategy addresses challenges such as outdated programming languages, poor integration capabilities, and inability to scale with business growth.
The choice between these approaches depends on identifying the primary source of system limitations. When legacy hardware presents the main roadblock, infrastructure modernization through strategies like lift and shift can provide immediate benefits. Conversely, when applications themselves lack essential features or architectural flexibility, application modernization becomes necessary.
Many organizations benefit from a hybrid approach, beginning with infrastructure modernization to establish a stable foundation before pursuing application-level changes. This staged methodology reduces risks while maximizing return on modernization investments.
Risk Assessment and Business Continuity Planning
Effective risk assessment forms the cornerstone of successful legacy modernization services. Organizations must evaluate multiple risk factors including operational disruptions, data migration challenges, security vulnerabilities, and potential system failures during transition periods.
Operational risks encompass the impact on day-to-day business processes, with more aggressive modernization strategies typically requiring extensive retraining and process adjustments. Organizations must balance the desire for modern capabilities against the reality of operational disruption and resource constraints.
Technical risks include data integrity concerns during migration, compatibility issues with existing integrations, and the possibility of introducing new bugs or vulnerabilities. Legacy systems that have operated reliably for years may contain undocumented dependencies or business logic that could be lost during aggressive modernization approaches.
Business continuity planning requires establishing fallback procedures, defining rollback strategies, and maintaining parallel systems during critical transition phases. Organizations should prioritize continuous updates and proactive technical debt management to prevent future legacy issues while implementing modernization initiatives.
The most effective risk mitigation strategies involve incremental modernization approaches that minimize disruptions while providing steady delivery of business value. This methodology allows for frequent reassessment and course correction, reducing the likelihood of catastrophic failures that could jeopardize business operations.
Technology Stack Powering Modern Application Architecture
Cloud Platforms and Infrastructure as a Service Solutions
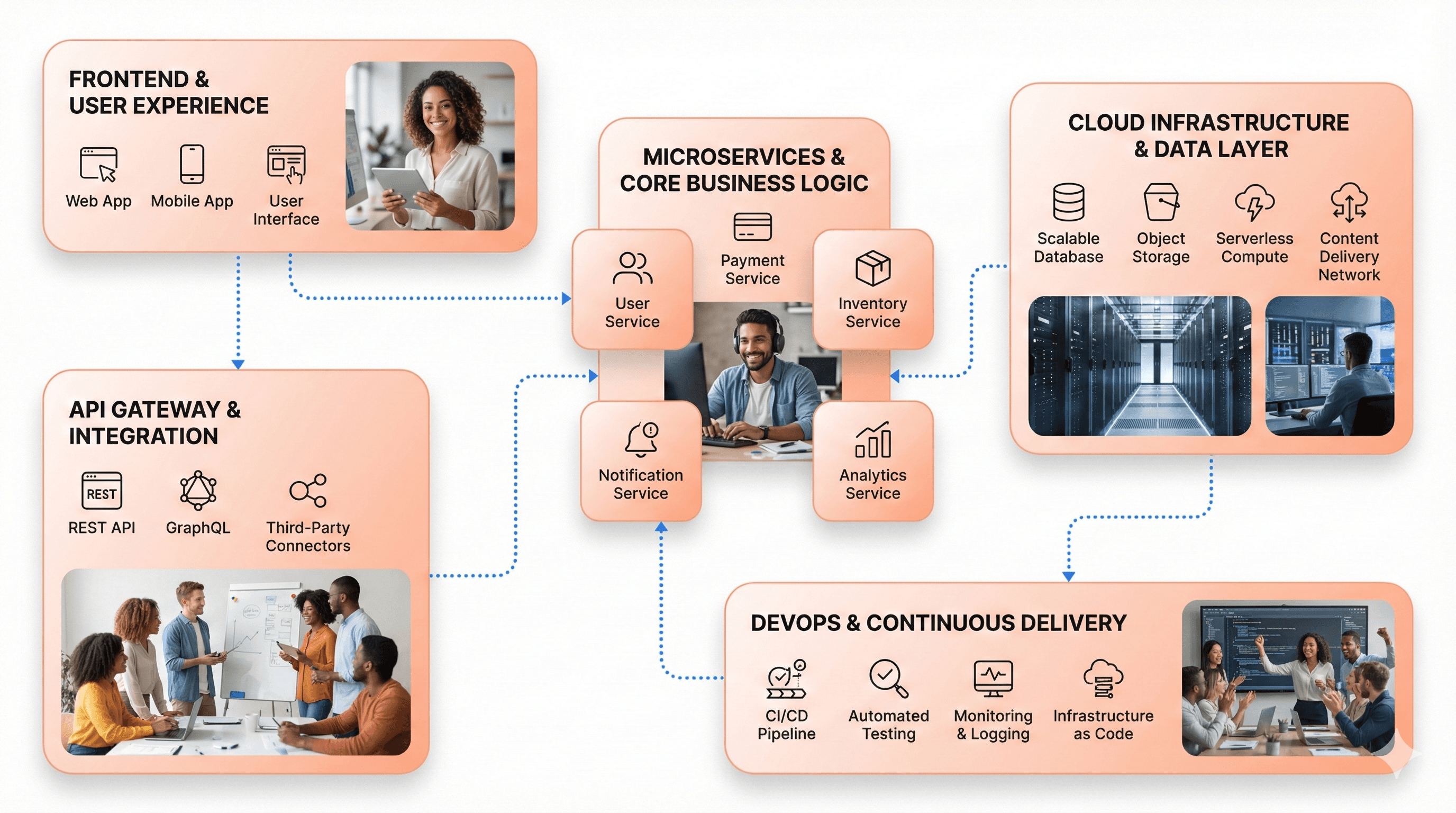
Cloud computing platforms like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) provide scalable infrastructure and a wide range of services for hosting, storage, and networking. These platforms serve as the foundation for modern application architectures, offering the flexibility and scalability that legacy systems often lack.
When evaluating cloud platforms for legacy modernization services, organizations must consider service offerings, pricing models, and geographic availability for their specific use case while considering vendor lock-in risks and multi-cloud strategies for flexibility. Development team expertise and learning curve for platform-specific services should be assessed alongside compliance requirements and security certifications for your industry.
Other notable platforms like Firebase, Cloudflare, and DigitalOcean are less popular but still widely used, offering specialized services that complement the major cloud providers. The key is to evaluate integration capabilities with existing systems and tools while reviewing the maturity and roadmap of services relevant to your architectural patterns.
Microservices Architecture and API-Driven Development
Microservices architecture breaks applications into small, independent services communicating via APIs and message queues. Each service owns its data and business capabilities, enabling fault isolation, technology diversity, and scalable components. This approach represents a fundamental shift from traditional monolithic architectures where all functionality was bundled into a single, tightly coupled unit.
The key difference lies in promoting loose coupling between components, enabling independent deployment, and supporting horizontal scaling across multiple servers. This allows each component to evolve, scale, and deploy independently, helping development teams respond quickly to changing business needs without impacting the entire application.
Service-oriented principles allow independent services to manage specific business capabilities, facilitating specialization and consistent API communication. Companies like Netflix and Amazon showcase the benefits of this architectural pattern, demonstrating how microservices can support rapid business evolution and scale.
However, implementing microservices requires robust service discovery, monitoring, and careful API design to maintain resilience and performance. The operational complexity grows with the number of services and deployment environments, necessitating sophisticated monitoring and management tools.
Containers, Kubernetes, and DevOps Integration
Container-based architecture packages applications with dependencies into portable containers managed by orchestration platforms like Kubernetes. This ensures consistent environments from development to production, supports both monolithic and microservices models, and facilitates faster deployment and scaling.
The top containerization technologies are Docker and Kubernetes, with other popular tools including Azure Container Apps, IBM Cloud Kubernetes Service, OpenShift Container Platform, Google Kubernetes Engine, and AWS Fargate. Containers share the host operating system's kernel, making them more lightweight and efficient than traditional virtualization approaches.
Orchestration—performed with tools like Kubernetes and Docker Swarm, is the automated deployment, scaling, and management of an app's services, components, and containers. Working across clusters of servers, orchestration tools ensure that applications run reliably and efficiently in cloud environments, simplifying the deployment process and allowing teams to focus on building and improving applications rather than dealing with infrastructure.
DevOps practices are deeply integrated into modern application architecture, enabling automated, continuous integration and delivery pipelines that allow teams to build, test, and deploy independently and frequently. The modular nature of modern applications aligns well with DevOps, as it encourages smaller, decoupled services that can be managed by cross-functional teams.
AI, Machine Learning, and Automation in Modernization
AI tools are transforming the development process, helping developers write code more efficiently, detect and fix issues faster, and deliver more reliable web applications in shorter timeframes. GitHub Copilot, powered by OpenAI's GPT, is a top choice for AI-driven development, with 55% of developer respondents using it in 2023 according to Stack Overflow surveys.
Other significant AI development tools include Tabnine, an AI-powered code completion tool, and Amazon CodeWhisperer, Amazon's code completion and suggestion tool. Snyk Code uses AI to analyze code repositories and identify security vulnerabilities and license issues, enhancing the security aspects of legacy modernization services.
Serverless functions, like AWS Lambda, offer scalable, event-driven processing without server management, enabling automation of various modernization tasks. Event-driven architecture uses events published to message brokers to enable asynchronous, loosely coupled communication, ideal for real-time data streaming and complex workflows that support patterns like event sourcing and CQRS for distributed transactions.
The adoption of AI and automation in modernization projects helps organizations manage the complexity of transitioning from legacy systems while maintaining delivery velocity and business continuity.
Execution Framework for Successful Legacy Modernization
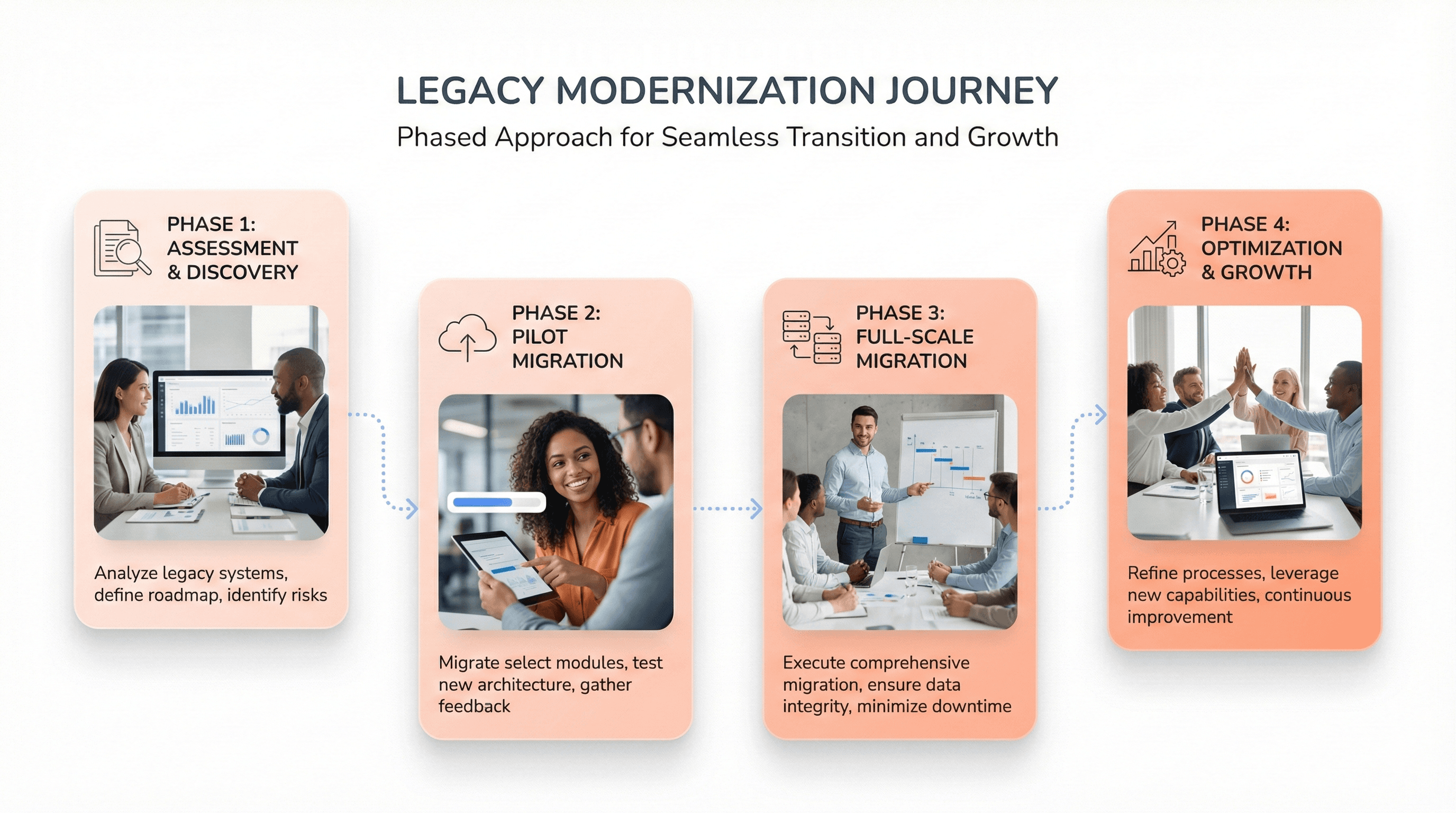
Assessment, Discovery, and Current State Analysis
Successful legacy modernization services begin with comprehensive portfolio discovery to establish a single source of truth for all applications and IT infrastructure. This initial inventory collection phase serves as the foundation for all subsequent modernization activities.
The assessment process involves four critical layers of analysis. At the application layer, teams identify programming languages, frameworks, runtime environments, and tools currently in use. The infrastructure layer requires mapping out operating systems, middleware, storage systems, and security dependencies. The data layer documentation encompasses data architecture including sensitivity classifications, security protocols, data flow patterns, database systems, volume requirements, and external data services that form the complete data ecosystem. Finally, the integration layer maps system interconnections, external system interfaces, API dependencies, data exchange patterns, authentication mechanisms, and trust zones of external systems.
Organizations can employ three primary inventory collection methods. Automated discovery tools provide efficient data gathering from SaaS and cloud APIs. Analysis and extraction from prior documents enables reverse engineering of architecture from past knowledge base sources and operations documentation. Manual discovery processes using surveys engage stakeholders to capture tribal knowledge and identify current pain points through structured questionnaires.
A comprehensive assessment evaluates multiple dimensions of the current state. Application architecture assessment examines technical foundations, architecture patterns, scalability capabilities, performance characteristics, resilience features, and security mechanisms. Cloud readiness assessment determines container readiness, API compatibility, data portability, and security compliance while assessing architecture compatibility and infrastructure requirements.
Goal Setting, Success Metrics, and Technology Selection
Now that we have covered the assessment phase, establishing clear objectives and measurable outcomes becomes critical for modernization success. Organizations must define strategic goals that align with business objectives while managing risks and ensuring operational continuity.
The goal-setting process prioritizes business needs over technology choices, ensuring a future-proof modernization approach. Key performance indicators should encompass operational efficiency improvements, cost reduction targets, security enhancement objectives, and scalability requirements. Organizations typically aim to reduce annual maintenance costs by up to 50% while achieving a 14% increase in annual revenue through modernization initiatives.
Financial planning requires careful consideration of cost structures including one-time migration expenses for rehosting, re-platforming, or refactoring activities. Ongoing operational costs encompass cloud services, infrastructure, and support requirements. Personnel and training investments focus on upskilling teams in DevOps, security, and cloud technologies.
Technology selection follows a strategic classification framework that assigns appropriate migration strategies to applications. The decision process evaluates candidates for rehosting (lift-and-shift), re-platforming opportunities, refactoring requirements, and replace/retire options based on technical and business criteria.
Success metrics should track quantifiable improvements including cost savings realization, performance enhancement measurements, business benefit achievement, and innovation value creation. Organizations pursuing modernization typically experience cloud-native cost reductions of up to 40% while improving performance and scalability through technologies like containers, Kubernetes orchestration, and microservices architectures.
Pilot Implementation and Proof of Concept Validation
With clear goals and technology strategies established, pilot implementation provides crucial validation before full-scale deployment. This phase emphasizes risk mitigation and business continuity through controlled testing environments that demonstrate modernization value while securing stakeholder buy-in.
Preparation activities include strategic team formation, tool selection, environment setup, and clear process definition to ensure implementation readiness. Organizations should start small and build on initial successes to showcase tangible benefits and gain support for expanding modernization efforts.
The pilot phase utilizes standardized migration templates based on the selected modernization strategy. For containerization initiatives, teams implement Docker and Kubernetes technologies that enable resource automation and change management optimization. API exposure facilitates integration by allowing existing applications to interact with modern systems, enhancing functionality while maintaining operational stability.
Incremental modernization approaches like the Strangler pattern enable gradual replacement of legacy systems by developing new features around existing infrastructure. This phased transformation approach allows step-by-step replacement while maintaining business operations and gradually redirecting traffic to modernized components.
Validation activities focus on performance optimization, security implementation, and thorough testing protocols. Cloud-native architectures facilitate seamless scaling and service integration, promoting agility in application management while ensuring consistent application performance during the transition period.
Full-Scale Migration with Continuous Testing and Optimization
Previously, we've established the foundation through assessment and proven concepts through pilot implementation. The full-scale migration phase requires systematic execution with robust monitoring frameworks and continuous optimization practices to ensure sustainable modernization outcomes.
Implementation execution follows a comprehensive process including migration execution, thorough testing and validation, performance optimization, and security implementation to ensure successful deployment. Architecture-driven DevOps practices should track the modernization roadmap with DevOps task status validation and continuous monitoring.
Operational framework development defines comprehensive operations models including operational procedures, support structures, monitoring frameworks, and incident management processes. This ensures sustainable application management while maintaining business continuity throughout the migration process.
Governance planning establishes robust decision frameworks, policy management processes, compliance controls, and risk management strategies to maintain operational integrity and regulatory compliance. Monitoring tools become essential for tracking progress during implementation, allowing for real-time adjustments to stay aligned with project goals.
Continuous optimization involves architecture observability practices that continually align operational services with business goals. By monitoring architecture drifts continuously, application services can be governed effectively for risk and cost management. Organizations should implement quarterly workload well-architected assessments to cut cloud waste by up to 30% while maintaining operational efficiencies.
The migration process emphasizes containerization and orchestration leveraging Kubernetes-based platforms that enable deployment and management of containerized applications, promoting portability, scalability, and efficient resource utilization. Modern development tools and APIs enable developers to build, test, and deploy applications efficiently within established CI/CD pipelines.
Overcoming Common Modernization Challenges
Data Migration Complexity and Integration Dependencies
Data migration represents one of the most challenging aspects of legacy modernization services. Legacy systems often contain complex data structures that are poorly documented and incompatible with modern technologies. These outdated schemas require extensive mapping, transformation, and validation to ensure data accuracy and consistency during the migration process.
The complexity deepens when dealing with legacy databases that have accumulated years of patches, customizations, and interdependencies. Organizations frequently discover that their data is tightly coupled with business logic embedded within the legacy system, making extraction and transformation particularly challenging. This creates a web of dependencies that must be carefully unraveled to prevent data corruption or loss.
To manage data migration effectively, organizations should prioritize careful data mapping and transformation processes that align legacy structures with modern schema requirements. Implementing automated migration tools can significantly reduce manual errors and accelerate the process while ensuring data integrity. Additionally, conducting thorough data cleansing during migration helps eliminate duplicates, inconsistencies, and outdated information that could compromise the new system's performance.
Change Management and Organizational Resistance
Organizational resistance poses a significant barrier to successful legacy modernization initiatives. Employees often resist change due to familiarity with existing systems and fear of disrupting established workflows. This resistance becomes particularly pronounced when modernization involves replacing systems that have been deeply integrated into daily operations for years or decades.
The challenge is compounded by skill gaps within organizations. As legacy systems rely on outdated programming languages and technologies, finding developers with necessary expertise becomes increasingly difficult. Many professionals skilled in legacy technologies are retiring, leaving fewer experts available to guide the transition while training new team members on both legacy and modern systems.
Effective change management requires comprehensive communication strategies that clearly articulate the benefits of modernization while addressing employee concerns. Organizations should invest in cross-training programs that help existing staff develop skills in both legacy and modern technologies. This approach ensures continuity during the transition while building internal capability for ongoing system management.
Budget Planning and Hidden Cost Management
Legacy modernization projects frequently exceed initial budget estimates due to hidden complexities and unforeseen dependencies. The true cost of modernization extends beyond obvious expenses like new software licenses and hardware upgrades to include specialized consultants, extended development timelines, and potential system downtime during migration.
Organizations often underestimate the resources required to address technical debt accumulated over years of system operation. This technical debt manifests as complex patches, quick fixes, and unsupported libraries that require significant effort to untangle and modernize. The complexity increases when dealing with monolithic architectures where tightly coupled components create cascading effects from seemingly minor changes.
To manage costs effectively, organizations should conduct thorough assessments of their current systems using six critical drivers: business value, technology obsolescence, operational risks, agility and scalability, cost efficiency, and regulatory compliance. This analysis helps identify the most critical areas for modernization while providing realistic cost projections. Breaking modernization into smaller, manageable phases allows for better budget control and reduces the risk of cost overruns.
Minimizing Business Disruption and Downtime Risks
Business continuity represents a paramount concern during legacy modernization, as system downtime can result in significant revenue losses and customer dissatisfaction. The risk of disruption is particularly high when modernizing mission-critical systems that support core business operations. Organizations must carefully balance the need for modernization with the imperative to maintain operational stability.
The TSB Bank incident in April 2018 illustrates the severe consequences of poorly managed system migrations. The bank's attempt to upgrade its computer system while simultaneously migrating customer records resulted in a major system crash, leaving customers unable to access their accounts and causing trading disruptions that lasted several days. The failed migration cost £330 million in direct expenses, with an additional £49.1 million lost to financial fraud during the outage.
To minimize disruption risks, organizations should adopt incremental modernization approaches such as the Strangler Fig pattern, which involves building new systems around existing ones and gradually replacing functionality rather than attempting complete system overhauls. This strategy allows legacy systems to continue operating while new components are implemented and tested. Comprehensive risk assessments should identify potential vulnerabilities early in the process, enabling organizations to develop mitigation strategies before issues impact operations.
Best Practices for Modernization Success
Aligning Technical Initiatives with Business Objectives
The most successful legacy modernization services focus on business value rather than purely technical improvements. Organizations that prioritize business-first modernization strategies see significantly better returns on their investments. When conducting comprehensive assessments, teams must map system components not just for technical complexity, but for business criticality and revenue impact.
Start by identifying which systems are actual blockers to growth versus those that simply need maintenance. As referenced in successful modernization projects, focus first on applications that are core to revenue, security, or customer experience. This approach ensures that technical efforts directly support strategic business goals rather than becoming isolated IT initiatives.
Engaging both IT and business stakeholders early in the process is crucial for maintaining this alignment. Business users bring essential context about workflows and requirements that technical teams might miss. This collaboration helps avoid the common trap of modernizing systems that don't meaningfully impact business operations.
Establishing Strong Governance and Security Frameworks
Security cannot be an afterthought in legacy modernization services. Modern systems often introduce new endpoints, APIs, cloud storage, and third-party integrations that legacy security models weren't designed to handle. Organizations must embed security considerations throughout the modernization process rather than treating them as final checklist items.
Effective governance requires establishing clear ownership and accountability structures. Successful modernization projects typically involve a senior sponsor who visibly owns the initiative and ties modernization milestones to specific business outcomes. This leadership backing becomes critical when projects encounter unexpected challenges or require additional resources.
Implementation should include security scans embedded directly in the DevOps pipeline, regular review of access controls for every new component or microservice, and involvement of compliance teams during architecture planning rather than just at audit time. This proactive approach prevents security gaps from emerging during the transformation process.
Phased Implementation and Stakeholder Buy-in Strategies
One of the primary reasons legacy modernization projects fail is attempting to transform everything simultaneously. Breaking modernization efforts into manageable phases significantly improves success rates and reduces overall risk. Successful organizations migrate by module rather than attempting wholesale monolith transformations.
Pilot rollouts with clear rollback plans provide essential learning opportunities and build confidence among stakeholders. These early wins help demonstrate value and generate momentum for larger transformation efforts. Building fast feedback loops through DevOps and CI/CD practices ensures that issues are identified and resolved quickly during each phase.
Stakeholder resistance often stems from fear of change rather than opposition to improvement. Teams that have adapted to legacy system quirks may view modernization as threatening rather than beneficial. Converting resistant voices into allies requires involving power users early in design phases and giving them ownership in the new system. Training alone isn't sufficient – teams need reassurance about their roles and value in the modernized environment.
Ongoing Testing, Validation, and Continuous Improvement
Testing becomes even more critical during legacy modernization because older systems often contain undocumented business logic that's been patched over years without proper test coverage. Every change introduces risk of breaking long-standing functionality that may not be immediately apparent.
Establishing comprehensive baselines before beginning modernization provides essential reference points for validation. Incremental testing approaches with continuous integration and delivery pipelines help identify issues before they impact production systems. This includes automated testing for functionality, performance, and security at each stage of the modernization process.
Post-migration monitoring and optimization represent ongoing commitments rather than one-time activities. Successful modernization requires tracking metrics, logs, and traces to ensure systems perform as expected in their new environments. Performance data analysis may reveal over-provisioned resources, memory leaks, or other optimization opportunities that weren't apparent during planning phases.
Modernization should be treated as an ongoing process rather than a completed milestone. Technology standards continue evolving, making continuous improvement essential for maintaining the benefits of modernization investments. Regular optimization cycles help organizations avoid accumulating new technical debt while maximizing the value of their modernized systems.
Selecting the Right Modernization Partner
Key Capabilities to Look for in Service Providers
When evaluating legacy modernization services providers, enterprises must prioritize partners with proven technical expertise across multiple transformation strategies. Leading providers should demonstrate mastery of the six modernization approaches: rehosting, replatforming, refactoring, rebuilding, replacing, and continuous optimization. Look for companies that offer AI-powered assessment tools, such as automated code analyzers and dependency mapping capabilities, which can significantly compress migration timelines and reduce defect rates.
Automation tooling represents a critical differentiator among service providers. Request demonstrations of GenAI-powered platforms that can decode source code, analyze complex system dependencies, and provide optimization recommendations. For instance, providers with proprietary automation suites can accelerate code conversion, data migration tasks, and cloud deployment while enforcing quality and security controls throughout the process.
Change management maturity is equally essential. Successful modernization extends beyond technical implementation to encompass comprehensive training, communications planning, and KPI frameworks that connect technical outputs to business outcomes. Evaluate whether prospective partners offer low-code DevSecOps frameworks with integrated policy checks, facilitating secure continuous integration and delivery from the first migrated release.
Regional Expertise and Compliance Requirements
Regional compliance capabilities are non-negotiable when selecting legacy modernization services partners. Different markets impose distinct regulatory requirements that directly impact modernization strategies and implementation approaches.
In the United States, providers must demonstrate expertise with regulations like HIPAA, SOX, and CCPA. The cloud-first policies and DevOps culture prevalent in U.S. markets require partners who can navigate intense competition and evolving customer expectations while maintaining strict compliance standards.
The United Arab Emirates presents unique challenges with initiatives like UAE Vision 2031 and Smart Dubai driving digital transformation. Service providers must understand data residency requirements and cybersecurity standards specific to banking, logistics, and healthcare sectors operating within the UAE's smart governance frameworks.
UK-specific expertise becomes crucial given the post-Brexit regulatory landscape and open banking requirements. Partners should demonstrate experience with GDPR compliance and understand how regulatory shifts impact legacy financial services, insurance, and government sector modernization initiatives.
Australian government agencies require providers familiar with the cloud-first policy for government services and compliance frameworks like IRAP. Understanding Australia's emphasis on digital innovation in healthcare, education, and public infrastructure ensures successful legacy system transformation while meeting citizen experience expectations.
Industry-Specific Experience and Track Record
Industry specialization significantly impacts modernization success rates. Financial services modernization requires deep understanding of COBOL-based banking software, core system dependencies, and regulatory compliance needs. Providers should demonstrate experience converting legacy loan systems to microservices architectures while maintaining transaction integrity and reducing processing times.
Healthcare sector expertise involves navigating complex patient data requirements, interoperability standards, and compliance with medical regulations. Successful providers have track records of modernizing hospital platforms, electronic health records, and healthcare management systems while ensuring data security and system availability.
Government and public sector modernization demands understanding of citizen service requirements, procurement processes, and security clearance protocols. Providers should showcase experience with government-led digital initiatives, smart city implementations, and public infrastructure modernization projects.
Retail and logistics modernization requires expertise in real-time tracking systems, supply chain optimization, and omnichannel customer experiences. Look for providers who have successfully modernized vessel tracking systems, inventory management platforms, and customer-facing applications while achieving measurable performance improvements.
End-to-End Support from Strategy to Implementation
Comprehensive service delivery models distinguish leading modernization partners from purely technical providers. End-to-end support begins with portfolio diagnostics and platform-aware migration planning, extending through implementation to post-migration optimization and continuous improvement.
Strategic planning capabilities should include AI-assisted code analysis, cloud-native framework selection, and phased execution roadmaps that deliver incremental business value. Providers must demonstrate ability to align transformation playbooks with enterprise goals while preserving business continuity during migration phases.
Implementation excellence requires modular service models and design-led planning approaches. Partners should offer flexible engagement models, from innovation labs to co-delivery arrangements, supporting transformation across regulated and high-availability environments. Structured parallel testing, secure migration protocols, and domain expertise ensure successful full-stack reengineering.
Post-implementation support encompasses continuous optimization, performance monitoring, and ongoing modernization initiatives. Leading providers offer self-funding models embedded within application services, emphasizing automation, rationalization, and cost control to reduce technical debt without major upfront investment. This approach ensures sustained value delivery and positions enterprises for future innovation cycles.
Conclusion
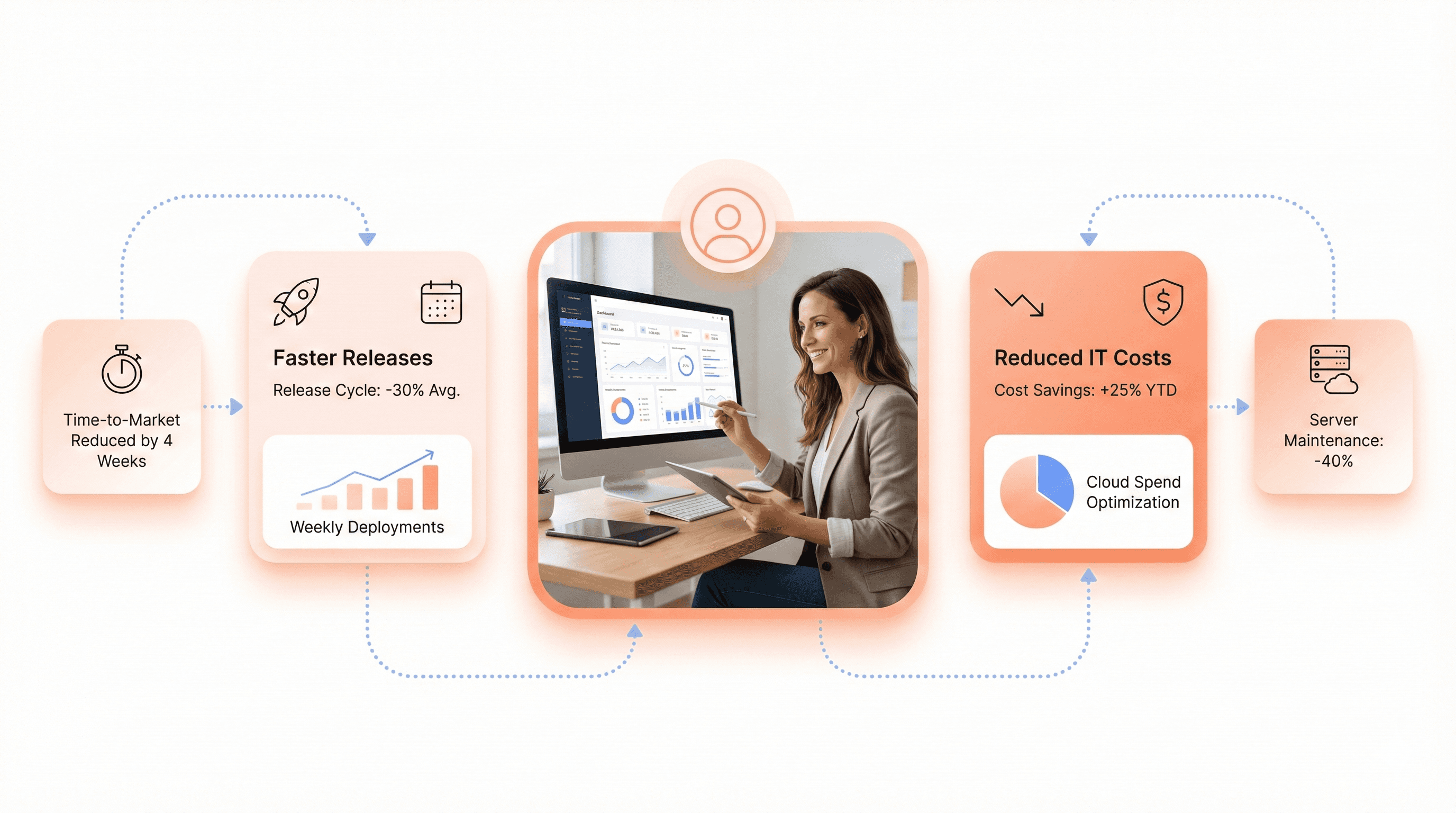
Legacy modernization is no longer optional, it's a strategic imperative for SaaS companies that want to remain competitive, secure, and agile in today's digital landscape. From understanding the fundamental challenges of legacy systems to implementing comprehensive modernization strategies, successful transformation requires careful planning, the right technology stack, and experienced partners who understand both the technical complexities and business objectives involved.
The path forward is clear: organizations that embrace modernization today will unlock improved performance, enhanced security, reduced operational costs, and accelerated innovation cycles. Whether you choose a lift-and-shift approach for quick wins or pursue a complete rebuild for maximum flexibility, the key is starting with a thorough assessment of your current systems and aligning modernization initiatives with your business goals. Don't let outdated infrastructure hold your SaaS platform back—begin your modernization journey with a trusted partner who can guide you through each phase of transformation and help you build a future-ready foundation for sustained growth.

About the author
Author Name:
Parth G
|
Founder of
Hashbyt
I’m the founder of Hashbyt, an AI-first frontend and UI/UX SaaS partner helping 200+ SaaS companies scale faster through intelligent, growth-driven design. My work focuses on building modern frontend systems, design frameworks, and product modernization strategies that boost revenue, improve user adoption, and help SaaS founders turn their UI into a true growth engine.
Is a clunky UI holding back your growth?
Is a clunky UI holding back your growth?
▶︎
Transform slow, frustrating dashboards into intuitive interfaces that ensure effortless user adoption.
▶︎
Transform slow, frustrating dashboards into intuitive interfaces that ensure effortless user adoption.






